computer access control systems

BYPASSING NETWORK ACCESS CONTROL SYSTEMS potx
... directly access some organizational resources for additional services. For example, access to DNS services requires access to a DNS server. While permitting access to such resources, the access ... NAC Systems Abstract The threat of viruses, worms, information theft and lack of control of the IT infrastructure has lead companies to implement security solutions to control the access ... tasked with one goal – controlling the access to a network using various methods and solutions. This whitepaper examines the different strategies used to provide network access controls. The flaws...
Ngày tải lên: 14/03/2014, 20:20

Access Control List - ACL
... 2: Router2(config) #access- list 1 deny 42.35.2.18 0.0.0.0 Router2(config) #access- list 1 permit any o Cách 3: Router2(config) #access- list 1 deny 42.35.2.18 Router2(config) #access- list 1 permit any ã Bc 10: t access- list ... một access- list chỉ chận địa chỉ IP 42.35.2.18 kèm theo lệnh access- list 1 permit any. Có 3 cách để thực hiện: o Cách 1: Router2(config) #access- list 1 deny host 42.35.2.18 Router2(config) #access- list ... cần thực hiện là “IP access- group 1 in”. Router2(config)#interface ethernet0 Router2(config-if)#ip access- group 1 in Router2(config-if)#exit 3 d. Kim nh li cỏc Standard Access List ã Bc 11:...
Ngày tải lên: 18/09/2012, 14:04

Bài thực hành Access Control List - ACL
... lệnh cần thực hiện là “IP access- group 1 in”. d. Kiểm định lại các Standard Access List 2 THỰC HÀNH Access Control List - ACL 1. Mục đích: làm quen với ACLs (Access Control List) và công dụng ... ACL) có thể chặn Router4 ping đến Router2. Tạo một access- list chỉ chặn địa chỉ IP 42.35.2.18 kèm theo lệnh access- list 1 permit any. ã Bc 10: t access- list va tạo vào giao tiếp FastEthernet 0/0. ... hợp chính xác” và bit 1 có nghĩa là “không cần xét”. Áp đặt access- list vào một giao tiếp trên Router bằng lệnh: ip access- group [access- list-number] [in | out] ã Chn mt host c bit: tất cả các...
Ngày tải lên: 19/09/2012, 09:21

Xe ô tô BMW X5 E70 SM 08_E70 Climate Control Systems
... Climate Control Systems Parked Car Ventilation The Parked Car stationary ventilation can be activated directly via the controller under timer control or via a remote start. When operated via the controller, ... output is controlled by the IHKA control unit by means of an infinitely variable control valve. The IHKA control command is converted into infinitely variable pro- portional powering of the control ... Blower power reduction to 50% of level two. 3. Switch off blower. 4 E70 Climate Control Systems Climate Control Systems Model: E70 Production: From Start of Production After completion of this...
Ngày tải lên: 19/10/2012, 13:50


CNC (Computer Numerical Control )
... MÁY CNC CHƯƠNG I :TỔNG QUAN VỀ MÁY CNC I.Lịch sử phát triển CNC (Computer Numerical Control ) có tiền thân là máy NC (Numerical Control) là các máy công cụ tự động dựa trên tập lệnh được mã hoá ... thường. III.Những khái niệm cơ bản và phân loại hệ điều khiển 1.Khái niệm cơ bản a.Khái niệm CNC CNC (Computer Numerical Control) là một dạng máy NC điều khiển tự động có sự trợ giúp của máy tính, mà trong ... chỉnh tốc độ cắt bề mặt bằng hằng số (Constant Surface Speed Control) . G97: Huỷ bỏ lệnh G96 (Constant Surface Speed Control Cancel). G98: Tốc độ tiến dao mm/phút (Feed per Minute). G99:...
Ngày tải lên: 27/04/2013, 17:23

Access Control Lists
... Copyright 2003, Cisco Systems, Inc. Case Study: Access Control Lists (ACLs) 1-15 To help with the physical layer design the company has ... Signature:_________________________Date:_______________ Copyright 2003, Cisco Systems, Inc. Case Study: Access Control Lists (ACLs) 1-9 For the demonstration, the company agrees that it is ... appropriate format ■ Provide a written final report Copyright 2003, Cisco Systems, Inc. Case Study: Access Control Lists (ACLs) 1-13 VLAN Port Assignments Update the switch tables, located...
Ngày tải lên: 16/10/2013, 20:15

Danh sách điều khiển truy cập (Access Control List)
... source 7.4.3.2 Lệnh ip access- group Lệnh này dùng để liên kết một danh sách truy cập đã tồn tại vào một giao diện. Cú pháp như sau: ip access- group access- list-No {in/out} o access- list-no: số ... đề tổng quát, cú pháp được mô tả như sau: access- list access- list- number {permit|deny} {test conditions} o access- list: là từ khóa bắt buộc o access- list-number: Lệnh tổng thể này dùng để ... giao diện. Cú pháp như sau: {protocol} access- group access- list-number Với: Protocol: là giao thức áp dụng danh sách truy cập Access- group: là từ khóa Access- list-number: Số hiệu nhận dạng...
Ngày tải lên: 19/10/2013, 00:20

Access control list
... lệnh: Router(config) #access- list access- list-number {deny | permit} source [ source-wildcard ] ……………… Router(config-if)#{protocol} access- group access- list-number {in | out} Hủy một ACL: Router(config)#no access- list access- list-number ... 0.0.0.0 eq 21 Config# access- list 100 permit IP any any Config#int s0 Config-if# ip access- group 100 IN 192.168.0.18 should be denied website of 192.168.0.34 On Router R3 Config# Access- list 100 deny ... access- list access- list-number 381 CHƯƠNG 7 407 Danh sách kiểm tra truy cập (ACL) Tạo ACL mở rộng S0 S0 E0 E0 A B 192.168.0.34 should be denied FTP of 192.168.0.18 On Router R1 Config# Access- list...
Ngày tải lên: 19/10/2013, 02:20

Basic Access Control
... Authorization Default router access first requires an administrator to gain user-level access before attempting privileged-level access. Thus, protecting and controlling user-level access into the routers ... methods for access are the lines— console port, auxiliary port, and virtual TTYs. Additional methods include HTTP, TFTP, and SNMP access, and each method of access requires its own access control configuration. Console ... rebooted. Privileged-level access control Once a user is logged into a line with user-level access, he can use the enable com- mand to attempt to gain privilege access. Privilege access allows a user...
Ngày tải lên: 27/10/2013, 07:15

Tài liệu AAA Access Control ppt
... leaving the accounting details for Chapter 11. AAA access control provides much greater scalability and functional- ity than the basic access control methods discussed in Chapter 3. AAA can use ... configured to use smart cards or token-based access control. A word of warning, however: due to the way that HTTP performs authentication, token-based access control cannot be used. AAA Security Checklist This ... rights reserved. AAA Security Checklist | 51 Token-Based Access Control An authentication method that offers additional security is token-based access con- trol. With this method, each user has a...
Ngày tải lên: 11/12/2013, 13:15

Tài liệu Control Systems Simulation using Matlab and Simulink pptx
... system 6 “Hands-on” Design of Control Systems “Hands on Design systems refers to directly working with the system to be controlled and trying a variety of controllers and control parameters. 6.1 Performance ... newtons/meter/sec ˙x 1 ˙x 2 ˙x 3 ˙x 4 = 0100 − k m 1 − c m 1 k m 1 c m 1 0001 k m 2 c m 2 − k m 2 − c m 2 x 1 x 2 x 3 x 4 + 0 1 m 1 0 0 u 4 K p K i K d controller 1 100 controller 2 10 0 0 controller 3 20 0 0 controller 4 20 1 0 controller 5 20 1 20 Plot all the unit-step output (y(t) ... value. We are interested in three types of controllers: 6.2.1 Proportional Control (P -control) : This is the simplest type of continuous control law. The controller output is made proportional to the...
Ngày tải lên: 12/12/2013, 07:15

Tài liệu An Introduction to Intelligent and Autonomous Control-Chapter 10: Learning Control Systems pdf
Ngày tải lên: 14/12/2013, 12:15

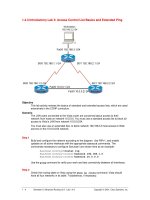
Tài liệu Access Control List Basics and Extended Ping ppt
... v2.0 - Lab 1.4.3 Copyright 2001, Cisco Systems, Inc. Access Control List Basics Access Control Lists (ACLs) are simple but powerful tools. When the access list is configured, each statement ... standard and extended access lists: Two-step process. First, the access list is created with one or more access- list commands while in global configuration mode. Second, the access list is applied ... list. It is not possible to reorder an access list, skip statements, edit statements, or delete statements from a numbered access list. With numbered access lists, any attempt to delete a single...
Ngày tải lên: 21/12/2013, 19:15

Tài liệu Access Control List Basics and Extended Ping doc
... v2.0 - Lab 1.4.3 Copyright 2001, Cisco Systems, Inc. Access Control List Basics Access Control Lists (ACLs) are simple but powerful tools. When the access list is configured, each statement ... standard and extended access lists: Two-step process. First, the access list is created with one or more access- list commands while in global configuration mode. Second, the access list is applied ... this step, you will configure an extended ACL to block access to a Web server. Before you proceed, issue the no access- list 50 and no ip access- group 50 commands on the Vista router to remove...
Ngày tải lên: 21/12/2013, 19:15

Tài liệu Control Systems Simulation using Matlab and Simulink doc
... in many real-life applications such as medical diagnosis [Slowinski, 1992], control algorithm acquisition and process control [Mrozek, 1992], and structural engineering [Arciszewski and Ziarko, ... Journal of Advanced Manufacturing, in press. Mrozek, A. 1992. Rough Sets in Computer Implementation of Rule-Based Control of Industrial Process. In Intelligent Decision Support — Handbook of ... Netherlands. Slowinski, R. and Stefanowski, J. 1989. Rough Classification in Incomplete Information Systems, Math- ematical & Computer Modeling, 12(10/11): 1347-1357. Yao, Y. Y., Wong, S. K. M., and Lin, T....
Ngày tải lên: 22/12/2013, 21:18

Tài liệu COMPUTER NUMERICAL CONTROL PROGRAMMING BASICS A Primer for the SkillsUSA/VICA Championships Steve docx
... into the work- piece. In incremental programming, the G91 command indicates to the computer and MCU (Machine Control Unit) that programming is in the incremental mode. Absolute program locations ... was standing in front of the machine while operating the controls. This design is no longer necessary, since in CNC the operator no longer controls the machine tool movements. On conventional machine ... developing a part program, Fig. 18. It is the part program that will be sent to the machine control unit by the computer, tape, diskette, or other input media. The programmer must first establish a...
Ngày tải lên: 25/12/2013, 05:16

Absolute stability of nonlinear control systems 2ed liao x yu p
Ngày tải lên: 01/01/2014, 17:47
