security in big data

security in big data
... centralized data mining and approaches for distributed data mining Distributed data mining can be further categorized into data mining over horizontally partitioned data and data mining over vertically ... employ inverse data mining such as inverse frequent set mining to generate data that cannot expose sensitive information By inverse data mining, we can customize the data...
Ngày tải lên: 17/12/2015, 17:48

Tài liệu Server Farm Security in the Business Ready Data Center Architecture v2.0 pdf
... invoked The Server Farm Security in the Business Ready Data Center Architecture v2.0 1-6 OL-7247-01 Chapter Server Farm Security Technology and Solution Overview LAN Security for the Server Farm ... the effect of these attacks Server Farm Security in the Business Ready Data Center Architecture v2.0 OL-7247-01 1-3 Chapter Server F...
Ngày tải lên: 09/12/2013, 17:15

Financial Services Authority Data Security in Financial Services pdf
... Page 14 Data Security in Financial Services ➤➤➤➤➤➤➤➤➤➤ 45 During 2007, FCID handled 187 financial crime cases and 56 of them involved data loss This made data loss the most common type of financial ... We noted during our visits a general shift in the financial services industry – including in small firms – from holding customer data in paper files to the electro...
Ngày tải lên: 06/03/2014, 19:20

security, privacy, & trust in modern data management
... searching large volumes of data for patterns, using techniques such as statistical analysis, machine learning and pattern recognition When data mining takes place in databases containing personal information, ... further investigation In this way, record matching could promote stereo-typing and lead to intrusive investigations 32 P Brey Data mining is a technique that is usually de...
Ngày tải lên: 25/03/2014, 12:08

Báo cáo khoa học: "Big Data versus the Crowd: Looking for Relationships in All the Right Places" docx
... architecture for never-ending language learning In Proceedings of the Conference on Artificial Intelligence, pages 1306–1313 J Finkel, T Grenager, and C Manning 2005 Incorporating non-local information into ... Empirical Methods in Natural Language Processing, pages 1013–1023 C Zhang, F Niu, C R´ , and J Shavlik 2012 Big e data versus the crowd: Looking for relationships...
Ngày tải lên: 30/03/2014, 17:20

Data Security in Payment Card Industry Dharshan Shantamurthy, SISA Information Security _part1 pptx
... Objective • Understanding the need for Security in Payment Card Industry and Overview of the Standards • Common Pitfalls in PCI DSS • Risk Assessment in PCI DSS Version 2.0 This is trial ... www.adultpdf.com Card Card Card Number Chip and PIN cards fall within scope of PCI DSS This is trial version www.adultpdf.com Expiry Date Card contd Magnetic Stripe is made up of “Trac...
Ngày tải lên: 19/06/2014, 21:20

Working with Database and Security in Java - Digital Signatures ppsx
Ngày tải lên: 02/08/2014, 08:21

Working with Database and Security in Java - Cryptography (tt) doc
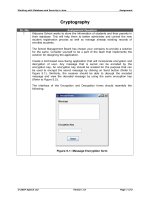
... Working with Database and Security in Java Assignment Figure 5.2: Message Decryption form © 2007 Aptech Ltd Version
Ngày tải lên: 02/08/2014, 08:21
Working with Database and Security in Java - Cryptography docx
... Working with Database and Security in Java Assignment Figure 5.2: Message Decryption form © 2007 Aptech Ltd Version
Ngày tải lên: 02/08/2014, 08:21
Working with Database and Security in Java - Java Security doc
Ngày tải lên: 02/08/2014, 08:21

Working with Database and Security in Java - Java Security docx
Ngày tải lên: 02/08/2014, 08:21



Emerging Security Issues In Modern Data Management Systems And Applications
... manage the data, extract meaningful information from the data, and make use of the extracted information Therefore, DMSs include database systems, data warehouses, and data mining systems Data could ... of security challenges that have not been solved yet 3.2 Data Warehousing and Data Mining: Security and Privacy Issues In this section we discuss security for...
Ngày tải lên: 13/08/2015, 10:01