security assessment case studies for implementing the nsa iam phần 2 ppt

security assessment case studies for implementing the nsa iam phần 2 ppt
... with scoping the assessment. www.syngress.com 20 Chapter 1 • Laying the Foundation for Your Assessment 28 6 _NSA_ IAM_ 01.qxd 12/ 15/03 3:15 PM Page 20 Q: How many hours does it take to do an IAM assessment? A: ... at all. From the Trenches… 28 6 _NSA_ IAM_ 02. qxd 12/ 11/03 3 :24 PM Page 49 three staff members for the duration .The pre -assessment process is cov-...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 3 ppt
... appropriate www.syngress.com 62 Chapter 2 • The Pre -Assessment Visit 28 6 _NSA_ IAM_ 02. qxd 12/ 11/03 3 :24 PM Page 62 homework and understand all the applicable regulations for that customer’s industry. Impact attributes are the ... agency www.syngress.com 1 02 Chapter 3 • Determining the Organization’s Information Criticality 28 6 _NSA_ IAM_ 03.qxd 12/ 11/03 3 :25 PM...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 1 docx
... Events 20 0 Customizing and Modifying the TAP to Suit the Job at Hand 20 0 Modifying the Nine NSA- Defined Areas 20 1 Level of Detail 20 1 Format 20 2 Case Study :The Bureau of Overt Redundancy 20 2 The ... Posture 28 2 The Yugo Implementation 28 3 The Ford Solution 28 4 The Cadillac Solution 28 4 Case Study: Medical Management 28 4 System Description 28 6 Inf...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 4 pot
... System Information Criticality 28 6 _NSA_ IAM_ 04.qxd 12/ 11/03 3 :27 PM Page 1 32 NOTE As the assessment team works with the customer to fill out the OICM, it’s normal for the customer to want to change ... 12/ 11/03 3 :25 PM Page 107 In the majority of assessments, the values for each block within the SCMs will be carried directly over from the OICM. Because of the...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 5 potx
... Router 1 provided the connectivity for the T1 from the Internet. Router 2 provided the connectivity for the medical center and colleges. Router 3 provided the connec- tivity for the dorm network.Translating ... significant damage to the organization. www.syngress.com The System Security Environment • Chapter 5 173 28 6 _NSA_ IAM_ 05.qxd 12/ 11/03 3 :28 PM Page 173...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 6 pdf
... Timeline 2- 4 Weeks 1 -2 Weeks 2- 8 Weeks Pre -Assessment On-Site Post Assessment Pre -Assessment Visit 1-5 Days 28 6 _NSA_ IAM_ 07.qxd 12/ 12/ 03 3: 32 PM Page 22 6 28 6 _NSA_ 06.qxd 12/ 15/03 11: 32 AM Page 21 8 (spouse, ... to the assessment approach to be able to accomplish the effort ■ Reiterates the benefits of the assessment process www.syngress.com Customer Ac...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 7 doc
... that www.syngress.com 27 2 Chapter 8 • Managing the Findings 28 6 _NSA_ IAM_ 08.qxd 12/ 15/03 5:03 PM Page 27 2 A. Not that I am aware of.They said they wanted to see the recommendations from this assessment first. But they ... every www.syngress.com 28 2 Chapter 8 • Managing the Findings 28 6 _NSA_ IAM_ 08.qxd 12/ 15/03 5:03 PM Page 28 2 Best Practices Checklist Preparing for...
Ngày tải lên: 13/08/2014, 15:21
security assessment case studies for implementing the nsa iam phần 8 docx
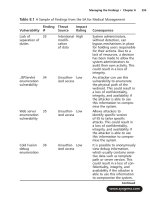
... on the “Ask the Author” form. You will also gain access to thousands of other FAQs at ITFAQnet.com. 28 6 _NSA_ IAM_ 08.qxd 12/ 15/03 5:03 PM Page 307 28 6 _NSA_ IAM_ 09.qxd 12/ 16/03 12: 58 PM Page 3 32 Table ... Chapter 9 329 28 6 _NSA_ IAM_ 09.qxd 12/ 16/03 12: 58 PM Page 329 ment team will need to be there to make the final decisions regarding your rec- ommendations .The seni...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 9 pot
... into the information security issues that are affecting the IISP environment. The assessment was conducted from May 1–June 28 , 20 02 .The assessment was an analysis of the current state of security ... Description The Introduction should include a description of the process used to conduct the assessment. In our case, we describe the NSA IAM as the methodo...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 10 pot
... information criticality information exchange, 23 1 23 2 information request, 69–70 Information Security (INFOSEC) assessment, 6, 23 documentation, 23 4 NSA IAM for, 2 roles/responsibilities, 23 4 23 5 Information Security ... baseline classes/categories, 23 2 24 6 in general, 23 2 23 3 management aspects, 23 3 23 6 operational aspects, 24 3 24 6 technical aspects, 23 6 2...
Ngày tải lên: 13/08/2014, 15:21
- a validated reference method for implementing the ich photostability study guidelines
- ombd on metal substrates case studies for rubrene perylene and pentacene
- look at case studies for ideas to make your interviewing stronger
- vendor products for implementing the trivadis blueprint
- case studies for pqd developing wowtab® odt
- selected case studies for sourcebook sections
- a case study for mitigating the impacts of sprawl
- implementing the order pipeline part 2