CLINICAL NEUROIMAGING: CASES AND KEY POINTS doc

CLINICAL NEUROIMAGING: CASES AND KEY POINTS doc
... White JS. USMLE Road Map Neuroscience. Lange Medical Books/McGraw Hill; 2002. CLINICAL NEUROIMAGING: CASES AND KEY POINTS David J. Anschel, MD Assistant Professor of Neurology State University ... sacral, and 1 coccygeal. Spinal nerves contain motor and sensory fibers, and have muscular and cutaneous branches. AUTONOMIC NERVES The autonomic nervous system implements hypot...
Ngày tải lên: 16/03/2014, 15:20

Tài liệu Activity 3.1: Identifying Data-Related Use Cases and Data Requirements docx
... Identifying Data-Related Use Cases and Data Requirements In this activity, you will analyze a set of use cases derived from the Ferguson and Bardell, Inc. case study and determine data requirements, ... Data-Related Use Cases and Data Requirements Exercise 1: Identifying Use Cases that Require Data In this exercise, you will identify data requirements from the provi...
Ngày tải lên: 21/12/2013, 06:16

Tài liệu Module 5: Analyzing Information: Use Cases and Usage Scenarios doc
... Objective To define use cases and provide examples. Lead-in Use cases describe the interaction between an actor and a system. Module 5: Analyzing Information: Use Cases and Usage Scenarios ... challenge and the vision statement. Verify that the use cases capture an entire process in detail. In the set of use cases, document the process in such a way that anyone can v...
Ngày tải lên: 21/12/2013, 06:17

Tài liệu Instructor Notes Module 5: Analyzing Information: Use Cases and Usage Scenarios doc
... the concepts of use cases and usage scenarios. ! Create use cases. ! Create usage scenarios. Materials and Preparation This section provides you with the materials and preparation needed ... call out use cases as a means to verify that students understand how to develop use cases. Once again, ensure that the students’ use cases are focused on describing the current sta...
Ngày tải lên: 17/01/2014, 09:20

Tài liệu Public-Key Cryptography and Key Management doc
... Elliptic-Curve Cryptography 3.6 Key Distributions and Management J. Wang. Computer Network Security Theory and Practice. Springer 2009 Chapter 3 Public -Key Cryptography and Key Management J. Wang. ... a common secret key • Bob and Malice have established a common secret key • Alice and Bob have not established any common secret key J. Wang. Computer Network Security...
Ngày tải lên: 17/02/2014, 14:20

Tài liệu Define a Primary Key and Other Indexes docx
... 2.3 Define a Primary Key and Other Indexes Indexes are used to improve performance when querying data, such as searching on fields and sorting information. The primary key is an index that ... ID. This How-To discusses what the best candidates are for primary keys, as well as how to create them and other indexes. You have created a base table and have even entered data into it....
Ngày tải lên: 14/12/2013, 20:16
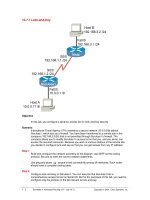
Tài liệu Lock-and-Key docx
... access list so that you, and you alone, can access the secured resources. Because you work at various stations at the remote site, you decide to configure lock -and- key so that you can get access ... The autocommand configuration is used to automate the process of creating a temporary access list entry. Upon authentication, SanJose1 executes the access- enable command and creates...
Ngày tải lên: 24/01/2014, 19:20

Tài liệu INSIDER’S GUIDE TO GRADUATE PROGRAMS IN CLINICAL AND COUNSELING PSYCHOLOGY doc
... master’s and doctorate in clinical psychology from the University of Rhode Island and completed his internship at the Brown University School of Medicine. He is Professor of Psychology and Distinguished ... residence, Psi Chi membership, and a close relationship between the student and former graduates of that program. Demand always exceeds supply in competitive clinical and c...
Ngày tải lên: 15/02/2014, 15:20

Tài liệu Taxation and Technology Transfer: Key Issues doc
... Peasants system land was owned collectively and each household was entitled to a share of the arable land. Peasants under China’s partially socialist system were thus protected from complete destitution and ... leaders, and, most important, to the territorial Partycommittees. These vertical and horizontal (tiaotiao and kuaikuai) lines of control sought to minimize the deviations of “...
Ngày tải lên: 19/02/2014, 08:20

Atopic Dermatitis – Disease Etiology and Clinical Management Edited by Jorge Esparza-Gordillo and Itaru Dekio doc
... ETIOLOGY AND CLINICAL MANAGEMENT Edited by Jorge Esparza-Gordillo and Itaru Dekio Atopic Dermatitis – Disease Etiology and Clinical Management 10 lymphocytes, eosinophils, and mononuclear ... Dermatitis – Disease Etiology and Clinical Management 8 Fig. 1. Flg ft mouse has a truncated and smaller profilaggin and a lack of filaggrin protein. 3.2 Flaky tail m...
Ngày tải lên: 08/03/2014, 00:20
- uniform customs and practice for documentary credits pdf
- uniform customs and practice for documentary credits 2012
- uniform customs and practice for documentary credits 600
- uniform customs and practice for documentary credits 600 pdf
- uniform customs and practice for documentary credits 500
- uniform customs and practice for documentary credits