using dynamic access control

learning microsoft windows server 2012 dynamic access control
... Third-party tools for Dynamic Access Control 98 Classification 98 Central Access Policy 99 RMS Protection 100 Auditing 101 Using DAC in SharePoint 102 BYOD – using Dynamic Access Control 103 Summary ... to implement a Dynamic Access Control solution Expression-based access rules By using expression-based access control, users or devices must satisfy conditions that we define to access files in ... www.it-ebooks.info Getting in Touch with Dynamic Access Control Dynamic Access Control (DAC) is a complete, end-to-end solution to secure information access and is not just another new feature...
Ngày tải lên: 01/08/2014, 16:59

MCSA 2012 DYNAMIC ACCESS CONTROL
... Dynamic Access Control 2/ Cấu hình Dynamic Access Control a Tạo Claim Types b Tạo Central Access Rule c Tạo Central Access Policy d Link Central Access Policy vào Group Policy 3/ Áp Central Access ... Central Access Rule, bạn kiểm tra lại điều kiện nhấn OK c Tạo Central Access Policy - Tiếp theo bạn cần tạo Central Access Policy Central Access Policy tập hợp gồm hay nhiều Central Access Rule ... tạo Central Access Policy chứa Central Access Rule vừa tạo - Ở khung Central Access Policies nằm góc bên phải, bạn chọn New, sau chọn Central Access Policy - Màn hình Create Central Access Policy,...
Ngày tải lên: 07/10/2014, 22:02

Using a DataGrid Control to Access a Database
... Click the addition icon to the left of the SelectCommand property to display the dynamic properties; one of the dynamic properties is the CommandText property, which contains the SELECT statement ... to display the properties for this object in the Properties window To enable sqlConnection1 to access the database, you need to set the password for the connection To this, add a substring containing ... or you can build it up visually Make sure all the columns are selected from the Customers table using the Customers box at the top left of the Query Builder Click OK to continue To check the rows...
Ngày tải lên: 07/11/2013, 10:15

MOB Subject 5 –Access methods Static and dynamic access techniques
Ngày tải lên: 17/09/2012, 09:13

Access Control List - ACL
... Router2(config) #access- list deny 42.35.2.18 0.0.0.0 Router2(config) #access- list permit any o Cách 3: Router2(config) #access- list deny 42.35.2.18 Router2(config) #access- list permit any • Bước 10: đặt access- list ... Router2 Tạo access- list chận địa IP 42.35.2.18 kèm theo lệnh access- list permit any Có cách để thực hiện: o Cách 1: Router2(config) #access- list deny host 42.35.2.18 Router2(config) #access- list ... hợp câu lệnh cần thực “IP access- group in” Router2(config)#interface ethernet0 Router2(config-if)#ip access- group in Router2(config-if)#exit d Kiểm định lại Standard Access List • Bước 11: Router4,...
Ngày tải lên: 18/09/2012, 14:04

Bài thực hành Access Control List - ACL
... Router2 để kiểm định access- list chạy giao tiếp, hiển thị cấu hình hoạt động • Xem access- list đặt vào giao tiếp • Xem access- list tạo router: e Tạo Access- List mở rộng ( Extended Access List) - Chỉ ... chuẩn (Standard ACL) chặn Router4 ping đến Router2 Tạo access- list chặn địa IP 42.35.2.18 kèm theo lệnh access- list permit any • Bước 10: đặt access- list vừa tạo vào giao tiếp FastEthernet 0/0 Chú ... đến nơi • Bước 13: huỷ access- list tạo giao tiếp Fa 0/0 Router2 lệnh “no ip access- group 1” • Bước 14: chuyển đến Router1 • Bước 15: cho phép telnet từ mạng 42.35.2.16 lệnh access- list 101 permit...
Ngày tải lên: 19/09/2012, 09:21

Access Control Lists
... Companies requirements using a VLSM design Subnets that will not be used are to be clearly identified in the table Copyright 2003, Cisco Systems, Inc Case Study: Access Control Lists (ACLs) 1-5 ... Case Study: Access Control Lists (ACLs) 1-17 Phase 7: Final demonstration The company now wants a demonstration of the complete company internetwork All devices are to be configured and access to ... Name Network Number Subnet Mask VLA N Switchport Type Encapsulation (if needed) Case Study: Access Control Lists (ACLs) 1-7 Location: Switch Name: Switch IP address: Interface/Sub interface Type/Port/Number...
Ngày tải lên: 16/10/2013, 20:15

Danh sách điều khiển truy cập (Access Control List)
... để xử lý vấn đề tổng quát, cú pháp mô tả sau: access- list access- list- number {permit|deny} {test conditions} o access- list: từ khóa bắt buộc o access- list-number: Lệnh tổng thể dùng để nhận ... dụng lệnh giao diện Cú pháp sau: {protocol} access- group access- list-number Với: Protocol: giao thức áp dụng danh sách truy cập Access- group: từ khóa Access- list-number: Số hiệu nhận dạng danh ... khối địa source 7.4.3.2 Lệnh ip access- group Lệnh dùng để liên kết danh sách truy cập tồn vào giao diện Cú pháp sau: ip access- group access- list-No {in/out} o access- list-no: số nhận dạng danh...
Ngày tải lên: 19/10/2013, 00:20

Access control list
... Router(config) #access- list access- list-number {deny | permit} source [source-wildcard ] ……………… Router(config-if)#{protocol} access- group access- list-number {in | out} Hủy ACL: Router(config)#no access- list ... 192.168.0.18 On Router R1 Config# Access- list 100 deny tcp 192.168.0.34 0.0.0.0 192.168.0.18 0.0.0.0 eq 21 Config# access- list 100 permit IP any any Config#int s0 Config-if# ip access- group 100 IN 192.168.0.18 ... 192.168.0.34 On Router R3 Config# Access- list 100 deny tcp 192.168 0.18 0.0.0.0 192.168.0.34 0.0.0.0 eq 80 Config# access- list 100 permit IP any any Config#int s0 Config-if# ip access- group 100 IN 407...
Ngày tải lên: 19/10/2013, 02:20

Basic Access Control
... This can be done using access control lists (ACLs) and the access- class command under the VTY lines To limit VTY access, you: Create an ACL Apply the ACL to all VTY lines with the access- class command ... methods for access are the lines— console port, auxiliary port, and virtual TTYs Additional methods include HTTP, TFTP, and SNMP access, and each method of access requires its own access control ... rebooted Privileged-level access control Once a user is logged into a line with user-level access, he can use the enable command to attempt to gain privilege access Privilege access allows a user...
Ngày tải lên: 27/10/2013, 07:15

Tài liệu AAA Access Control ppt
... 51 Friday, February 15, 2002 2:53 PM Token-Based Access Control An authentication method that offers additional security is token-based access control With this method, each user has a smart card ... configured to use smart cards or token-based access control A word of warning, however: due to the way that HTTP performs authentication, token-based access control cannot be used AAA Security Checklist ... authorized to use the EXEC prompt to execute commands Without access to an EXEC prompt, even users who are successfully 46 | Chapter 5: AAA Access Control This is the Title of the Book, eMatter Edition...
Ngày tải lên: 11/12/2013, 13:15

Tài liệu Display Data Using the Repeater Control pptx
... Events by Using ItemCommand When you're using buttons, you can program the response for when the buttons are pressed by using the ItemCommand event This event is raised for all the controls that ... is displayed using the Repeater control This list is displayed below the regions and contains the territories for the region clicked (see Figure 5.6) Figure 5.6 Another Repeater control is utilized ... solution From the main page, click on the hyperlink with the caption How-To 5.4: Display Data Using the Repeater Control You will then see a page open displaying a list of the regions (see Figure 5.5)...
Ngày tải lên: 14/12/2013, 20:16


Tài liệu Using Common Dialog Controls ppt
... PrintDocument controls Use a PrintDialog control Display MemberForm in the Design View window In the Toolbox, expand the Printing category Drag a PrintDialog control onto the form The control appears ... idiom that you saw earlier, when using the SaveFileDialog control Use a PrintDocument control Return to the Design View window Click and drag a PrintDocument control from the Printing category ... Another control appears under the form, called printDocument1 Using the Properties window, change the name of this control to printDocument Clear the DocumentName property Click the printDialog control...
Ngày tải lên: 15/12/2013, 00:15
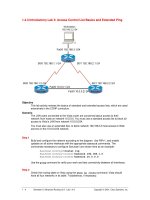
Tài liệu Access Control List Basics and Extended Ping ppt
... Access Control List Basics Access Control Lists (ACLs) are simple but powerful tools When the access list is configured, each statement in the ... standard and extended access lists: Two-step process First, the access list is created with one or more access- list commands while in global configuration mode Second, the access list is applied ... the list It is not possible to reorder an access list, skip statements, edit statements, or delete statements from a numbered access list With numbered access lists, any attempt to delete a single...
Ngày tải lên: 21/12/2013, 19:15

Tài liệu Access Control List Basics and Extended Ping doc
... Access Control List Basics Access Control Lists (ACLs) are simple but powerful tools When the access list is configured, each statement in the ... standard and extended access lists: Two-step process First, the access list is created with one or more access- list commands while in global configuration mode Second, the access list is applied ... the list It is not possible to reorder an access list, skip statements, edit statements, or delete statements from a numbered access list With numbered access lists, any attempt to delete a single...
Ngày tải lên: 21/12/2013, 19:15

Tài liệu The 20 Minute Guide to Using MS Access 2007 pptx
... Learning Microsoft Access is now simpler than ever Begin today and get your data in order fast http:/ /access- databases.com/ms -access- tutorial/ Contents What is a database? Access 2007 ... Learning Microsoft Access is now simpler than ever Begin today and get your data in order fast http:/ /access- databases.com/ms -access- tutorial/ For software, ebooks and training on MS Access please ... – a table in Access is a container with columns such as name, address etc Tables are the most important object in MS Access and are a useful starting point for any new database Access will ask...
Ngày tải lên: 24/12/2013, 02:15

Tài liệu Edit and Update Using Data Bound Controls pdf
... all the controls on the form and uses the TypeOf condition to check whether the current control is a text box It also ensures that the control is not the txtCustLimit text box If the control ... Boolean) Dim oCurr As Object '- Loop through each of the controls on the form For Each oCurr In Me.Controls() '- Check to see if the control is a text box If TypeOf oCurr Is TextBox And oCurr.Name ... the changes back to the server ADO.NET works using disconnected data When you create a dataset by using a data adapter, the data is actually created using XML To see proof of this, take a look...
Ngày tải lên: 24/12/2013, 06:17

Tài liệu Network Virtualization — Access Control Design Guide pdf
... the access control method to provide holistic control over client access to the network 802.1X always assumes a supplicant at the edge 802.1X can give customers ubiquitous, port-based access control ... EAP-Identity-Response EAP-Identity-Failure RADIUS -Access- Request RADIUS -Access- Reject RADIUS -Access- Request RADIUS -Access- Reject RADIUS -Access- Request RADIUS -Access- Reject EAP-Identity-Request EAP-Identity-Response ... deployment This design guide also introduces other clientless methods of access control to provide access as well This form of access control is device-specific in nature, and is discussed in the wired...
Ngày tải lên: 17/01/2014, 09:20