security apis in java 2

Working with Database and Security in Java - Digital Signatures ppsx
Ngày tải lên: 02/08/2014, 08:21

Working with Database and Security in Java - Cryptography (tt) doc
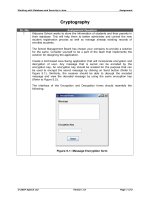
... Working with Database and Security in Java Assignment Figure 5 .2: Message Decryption form © 20 07 Aptech Ltd Version 1.0 Page of ...
Ngày tải lên: 02/08/2014, 08:21
Working with Database and Security in Java - Cryptography docx
... Working with Database and Security in Java Assignment Figure 5 .2: Message Decryption form © 20 07 Aptech Ltd Version 1.0 Page of ...
Ngày tải lên: 02/08/2014, 08:21
Working with Database and Security in Java - Java Security doc
Ngày tải lên: 02/08/2014, 08:21

Working with Database and Security in Java - Java Security docx
Ngày tải lên: 02/08/2014, 08:21



MVC architecture struts framework in java (J2EE)
... 16 1 .2 Controller 17 1.3 Model 20 Triển khai ứng dụng 23 2. 1 Cơ sở liệu 23 2. 2 Bố trí tập tin Eclipse 23 2. 3 Kết 24 Phần VI ... dụng : 2. 1 Cơ sở liệu Cơ sở liệu Access: members.mdb có bảng accounts 2. 1 Bố trí tập tin Eclipse : Trang 23 10 /20 07 MVC Architecture & Struts Framework in J2EE (Java) 2. 3 Kết quả: Trang 24 10 /20 07 ... in J2EE (Java) 10 /20 07 } public String execute() throws Exception{ System.out.println("execute() in Employee Action"); return SUCCESS; } public String input() throws Exception{ System.out.println("input()...
Ngày tải lên: 23/11/2012, 13:46

MVC Architecture & Struts Framework In Java(J2EE)
... 16 1 .2 Controller 17 1.3 Model 20 Triển khai ứng dụng 23 2. 1 Cơ sở liệu 23 2. 2 Bố trí tập tin Eclipse 23 2. 3 Kết 24 Phần VI ... dụng : 2. 1 Cơ sở liệu Cơ sở liệu Access: members.mdb có bảng accounts 2. 1 Bố trí tập tin Eclipse : Trang 23 10 /20 07 MVC Architecture & Struts Framework in J2EE (Java) 2. 3 Kết quả: Trang 24 10 /20 07 ... in J2EE (Java) 10 /20 07 } public String execute() throws Exception{ System.out.println("execute() in Employee Action"); return SUCCESS; } public String input() throws Exception{ System.out.println("input()...
Ngày tải lên: 27/04/2013, 10:41

MVC Architecture & Struts Framework In Java(J2EE)
... 16 1 .2 Controller 17 1.3 Model 20 Triển khai ứng dụng 23 2. 1 Cơ sở liệu 23 2. 2 Bố trí tập tin Eclipse 23 2. 3 Kết 24 Phần VI ... dụng : 2. 1 Cơ sở liệu Cơ sở liệu Access: members.mdb có bảng accounts 2. 1 Bố trí tập tin Eclipse : Trang 23 10 /20 07 MVC Architecture & Struts Framework in J2EE (Java) 2. 3 Kết quả: Trang 24 10 /20 07 ... in J2EE (Java) 10 /20 07 } public String execute() throws Exception{ System.out.println("execute() in Employee Action"); return SUCCESS; } public String input() throws Exception{ System.out.println("input()...
Ngày tải lên: 27/04/2013, 15:35

Security Issues in Wireless Systems
... [14–16] 12. 5 Mobile IP Mobile IP was developed in response to the increasing use of mobile computers in order to enable computers to maintain Internet connection during their movement from one Internet ... possible by using encryption algorithms Integrating L2TP with IPSec offers the ability to use L2TP as a tunneling protocol; however, securing the data is achieved using an IPSec scheme Using L2TP as ... enterprise management [21 ] VPNs provide the following main advantages [21 ,22 ]: † Security By using advanced encryption and authentication schemes, VPNs can secure data from being accessed by hackers...
Ngày tải lên: 29/09/2013, 21:20

Object Orientation in Java
... abstract classes and interfaces 625 0CH 12. qxd 2/ 23/06 11 :27 AM LESSON Page 57 12 ■■■ More OO in Java Interfaces and Abstract Classes I n Java there is officially no “multiple inheritance.” You may ... setName(String name); } 57 625 0CH 12. qxd 58 2/ 23/06 11 :27 AM Page 58 LESSON 12 ■ MORE OO IN JAVA INTERFACES AND ABSTRACT CLASSES Notice how I have an abstract method defined (setName(String name)) ... more exceptions than the method in the superclass (We’ll cover exception handling in Lesson 14.) 625 0CH 12. qxd 2/ 23/06 11 :27 AM Page 59 LESSON 12 ■ MORE OO IN JAVA INTERFACES AND ABSTRACT CLASSES...
Ngày tải lên: 05/10/2013, 10:20

XML programming in Java
... (line,line,line,line, line,line,line,line, line,line,line,line, line,line) > 32 ... saxCounter extends HandlerBase { int int int int int int int int int int startDocumentEvents = 0; endDocumentEvents = 0; startElementEvents = 0; endElementEvents = 0; processingInstructionEvents = 0; characterEvents ... head. I have seen roses damasked, red and white, But no such roses see I in her cheeks. And in some perfumes is there more delight Than in the...
Ngày tải lên: 22/10/2013, 15:15

Software architecture design pattern in java (giaotrinhchinh)
... representing an inner class The notation shown in Figure 2. 3 is used in this book to represent an inner class, where the inner class is placed in the operations section of class in which the inner ... can be drawn in two ways depending on how the interface is depicted Using a closed, hollow arrowhead pointing from the implementing class to the interface with a dashed line With a line and a circle, ... to thank the managing editor, Claire Miller, for her invaluable advice and contribution in arranging the book in a presentable form My sincere thanks to Linda Rising for writing the Foreword I...
Ngày tải lên: 07/12/2013, 11:57

Thinking in Java
... 20 6 The comma operator 139 Constructor initialization 20 8 Array initialization 21 6 Final methods 28 6 Multidimensional arrays 22 2 Final classes 28 9 Summary 22 5 Exercises 22 6 ... Exercises 22 Multimedia CD ROM 23 Source code 23 Coding standards 25 Java versions .26 Seminars and mentoring 26 Errors 27 Note on the cover design 27 Acknowledgements 28 1: Introduction ... syntax 26 1 Initializing the base class 26 4 Combining composition and inheritance 26 7 Guaranteeing proper cleanup 26 9 Name hiding 27 3 Choosing composition vs inheritance 27 4 protected...
Ngày tải lên: 10/12/2013, 14:44

Thinking In Java
... combining Interfaces 23 3 Adapting to an interface 23 4 Fields in interfaces 23 5 Initializing fields in interfaces 23 6 Nesting interfaces 23 7 Interfaces and factories 23 9 Summary 24 1 ... Interfaces 21 9 Abstract classes and methods 21 9 Interfaces 22 2 Complete decoupling 22 5 “Multiple inheritance” in Java 23 0 Extending an interface with inheritance 23 1 Name ... 1036 Thinking in Objects seminar 1036 Thinking in Enterprise Java 1036 Thinking in Patterns (with Java) 1037 Thinking in Patterns seminar 1037 Design consulting and reviews...
Ngày tải lên: 27/12/2013, 17:00

Tài liệu Security Threats in Mobile Ad Hoc Network doc
... implementation of routing protocol is overwhelmed 21 Security Threats in Mobile Ad Hoc Networks Chapter Security Threats in Network Layer 6 .2. 2 Routing Cache Poisoning Attack Routing cache poisoning attack ... 20 6 .2. 1 Routing Table Overflow Attack 21 6 .2. 2 Routing Cache Poisoning Attack 22 6 .2. 3 Attacks on Particular ... bits within this period to incur bit errors in a victim’s link layer frame via wireless interference [16] 5 .2 Threats in IEEE 8 02. 11 WEP The first security scheme provided by IEEE 8 02. 11 standards...
Ngày tải lên: 16/01/2014, 16:33

Tài liệu Fundamentals of OOP and Data Structures in Java Richard Wiene ppt
... void setLine1 (Line line1) { this.line1 = line1; } public void setLine2 (Line line2) { this.line2 = line2; } public String toString () { return ''line1: " + line1 + " line2: " + line2; } public ... Line(pt1, pt2); Line line2 = new Line(pt3, pt4); Line line3 = new Line(pt5, pt6); LineHolder lineHolder1 = new LineHolder(line1, line2); LineHolder lineHolder2; lineHolder2 = (LineHolder) lineHolder1.clone(); ... line1, line2; // Constructor public LineHolder (Line line1, Line line2) { this.line1 = line1; this.line2 = line2; } // Methods public void setLine1 (Line line1) { this.line1 = line1; } Page 27 ...
Ngày tải lên: 14/02/2014, 04:20