schemas database users and security domains

Working with Database and Security in Java - Cryptography (tt) doc
Ngày tải lên :
02/08/2014, 08:21
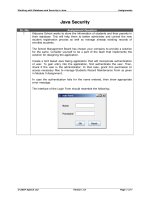
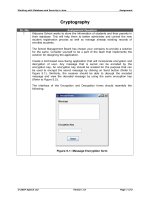
... Working with Database and Security in Java Assignment Figure 5.2: Message Decryption form © 2007 Aptech Ltd Version...
- 2
- 310
- 0
Working with Database and Security in Java - Cryptography docx
Ngày tải lên :
02/08/2014, 08:21
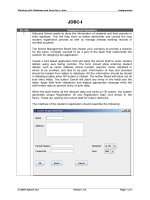
... Working with Database and Security in Java Assignment Figure 5.2: Message Decryption form © 2007 Aptech Ltd Version...
- 2
- 319
- 0

User and Security Management
Ngày tải lên :
11/09/2012, 13:54
... thành viên vai trò db_owner db_securityadmin: Vai trò cho phép người dùng quản lý tất vai trò thành viên chúng Vai trò cho phép gán quyền hạn cho vai trò Nếu User and Security Management 84 có người ... Database Design and Implementation with SQL Server b c a b c d Database Server 10 Quyền hạn cho phép người dùng xoá tạo lập đối tượng CSDL? Statement permissions User permissions Database permissions ... and Security Management 92 Bài tập Taok lập đăng nhập ‘Frodo’ T-SQL (Gợi ý: Sử dụng thủ tục sp_addlogin ) Tạo lập vai trò ‘Manager’ cho NETDOMAIN thêm thành viên ‘Assistant’ ‘Supervisor’ 93 Database...
- 17
- 1.1K
- 3

Question Bank Adv .Net and Security in .Net Project
Ngày tải lên :
09/04/2013, 09:10
... into a PE file has versioning and an extension of exe permissions [1.5] handles security b) The *.exe file in NET e) All of the above Framework is the same as a standalone executable created by ... ServiceProcessInstaller and ServiceInstaller must be inherited a) Only statements and are d) Statements 1, 2, are true true b) Only statements and are e) None of the above is true true c) Only statements and are ... handler methods used [2.5] for windows services? a) To invoke the methods c) To invoke the methods OnPause() and OnPause() and OnContinue(), the property OnContinue(), the property CanPauseAndContinue...
- 131
- 507
- 0

Java and Security
Ngày tải lên :
29/09/2013, 08:20
... refer to the JDK documentation and the security path of the Java Turorial at http://java.sun.com/docs/books/tutorial /security1 .2/index.html Security Problems and Java Security Testing Finally, the ... comes with the JDK and that provides you with a GUI tool for creating and maintaining policy files keytool—Used to create digital signatures and key pairs and to manage the keystore database jarsigner—Allows ... for testing and not deployed grant { permissionjava .security. AllPermission; }; Security Tools The JDK comes with several tools to help you manage the security of code that you write and wish to...
- 15
- 527
- 0

Oracle Database Backup and Recovery Advanced User’s Guide
Ngày tải lên :
16/10/2013, 11:15
... command to back up database files and archived redo logs Chapter 17, "Performing User-Managed Database Flashback and Recovery" This chapter describes how to use the SQL*Plus FLASHBACK DATABASE and ... primary database that is updated using archived logs created by the primary database RMAN can create or back up a standby database You can fail over to the standby database if the primary database ... to the Target Database and Recovery Catalog from the Command Line 5-3 vi Connecting to the Target Database and Recovery Catalog from the RMAN Prompt Connecting to an Auxiliary Database ...
- 586
- 728
- 2

Oracle Database Backup and Recovery Basics
Ngày tải lên :
18/10/2013, 17:15
... Copies and Backup Sets Full and Incremental Datafile Backups RMAN Backups and Tags Backing Up Database Files and Archived Logs with RMAN Making Consistent and ... Recovery Database Restore and Recovery with RMAN: Overview Scope and Limitations of this Chapter Restore and Recovery with Enterprise Manager Preparing and Planning Database ... for database administrators who perform backup and recovery of an Oracle database server To use this document, you need to know the following: s s Relational database concepts and basic database...
- 216
- 555
- 3

Apress - Pro SQL Server 2008 Relational Database Design and Implementation (2008)01
Ngày tải lên :
29/10/2013, 15:15
... Relational Database Design and Implementation Louis Davidson With Kevin Kline, Scott Klein, and Kurt Windisch 8662FM.qxp 7/28/08 6:19 PM Page ii Pro SQL Server 2008 Relational Database Design and Implementation ... Data Structures Database and Schema Tables, Rows, and Columns The Information ... 91 Identifying Attributes and Domains 98 Identifying Business Rules and Processes 108 Identifying...
- 15
- 509
- 0

Apress - Pro SQL Server 2008 Relational Database Design and Implementation (2008)02
Ngày tải lên :
29/10/2013, 15:15
... on database design Louis’s primary areas of interest are database architecture and coding in T-SQL, and he has experience designing many databases and writing thousands of stored procedures and ... Server 2005 Database Design and Optimization (Apress, 2006), and Database Benchmarking: Practical Methods for Oracle & SQL Server (Rampant, 2007) Kevin contributes to SQL Server Magazine and Database ... times, we’ll discuss, debate, and celebrate the topic of database design and how critical it is for any datacentric application Database design is part science and part art There’s a science...
- 15
- 535
- 0

Apress - Pro SQL Server 2008 Relational Database Design and Implementation (2008)03
Ngày tải lên :
08/11/2013, 21:15
... part of the security strategy (e.g., only this category of users should be able to access these tables) Expanding on that final point, a security plan ought to be built during this phase and used ... Structures This section introduces the following core relational database structures and concepts: • Database and schema • Tables, rows, and columns • The Information Principle • Keys • Missing values ... schema You use schemas to group objects in the database with common themes or even common owners All objects on the database server can be addressed by knowing the database they reside in and the schema...
- 15
- 514
- 0

Apress - Pro SQL Server 2008 Relational Database Design and Implementation (2008)04
Ngày tải lên :
08/11/2013, 21:15
... addressee’s name and address and the date the item was sent Be careful when choosing a natural key Ideally, you are looking for something that is stable, that you can control, and that is definitely ... always have some element that is just randomly chosen, and it should never be based on data that can change If your driver’s license number were a smart key and decoded to include your hair color, ... some youth and we folks whose hair has turned a different color) No, this value is good only for looking you up in a database Usually a true surrogate key is never shared with any users It will...
- 5
- 525
- 0

Tài liệu Module 4: Setting Up and Administering Users and Groups docx
Ngày tải lên :
10/12/2013, 16:15
... Setting Up and Administering Users and Groups v Module Strategy Use the following strategy to present this module: ! Introduction to Users and Groups In this topic, you will introduce users and groups ... Module 4: Setting Up and Administering Users and Groups Introduction to User Accounts and Groups Slide Objective To identify the purpose of user accounts and groups Users Users Group Group Shared ... User and Computers Active Directory Domains and Trusts Action View Active Directory Domains and Trusts Properties Name Type UPN Suffixes domain.DNS contoso.msft Active Directory Domains and Trusts...
- 60
- 486
- 0

Tài liệu Operational Administration Recovery and Security ppt
Ngày tải lên :
11/12/2013, 00:15
... commands You can mount filesystems, create directories, move files, and edit files using vi You can apply the fdisk and fsck commands to various hard disks and partitions A few other basic commands ... nightmare and a major loss of service for your users Understanding these tools is fundamental to getting through the RHCE Debug exam CERTIFICATION OBJECTIVE 11.01 Services and Special Users The ... Administration Recovery and Security T he themes of this chapter are security and recovery These are two critical concepts for the RHCE exam This continues the discussion of system security started...
- 42
- 420
- 0