pd and look ahead la algorithms

Báo cáo khoa học: "Fast and Scalable Decoding with Language Model Look-Ahead for Phrase-based Statistical Machine Translation" potx
... compare Moses and four different setups of our decoder: LM score pre-sorting switched on or off without LM look- ahead and both LM look- ahead methods with LM score pre-sorting We translated the test ... phrase-based machine translation Both pre-sorting the phrase translation candidates with an LM score estimate and LM look- ahead during search are shown to have a positive effect on translation speed We ... Statistical Machine Translation, pages 64–71, New York City, June [Ortmanns et al.1998] S Ortmanns, H Ney, and A Eiden 1998 Language-model look- ahead for large vocabulary speech recognition In...
Ngày tải lên: 23/03/2014, 14:20

Expect, Hope and Look forward to
... (Tôi mong sớm nhận hồi âm anh/chị) • I am looking forward to getting information from you soon (Mình mong sớm nhận thông tin cậu.) Trên khác...
Ngày tải lên: 11/11/2013, 00:11

Tài liệu Production Planning and Scheduling Using Genetic Algorithms doc
... random and inserts it in a random position Displacement mutation selects a substring at random and inserts it in a random position Reciprocal exchange mutation selects two positions at random and ... weight and processing time For given two jobs i and j, there are four basic patterns of ordering relations of them wi Ն wj and pi Ն pj wi Ն wj and pi Ͻ pj wi Ͻ wj and pi Ն pj wi Ͻ wj and pi Ͻ ... missing machine for a chromosome, a random replacement mutation operator is used The mutation operator first selects a gene randomly and then replaces it with a random integer from the set M, as shown...
Ngày tải lên: 25/12/2013, 19:15

Report of the Special Rapporteur on the promotion and protection of the right to freedom of opinion and expression, Frank La Rue* ppt
... rights law; and the availability of the necessary infrastructure and information communication technologies, such as cables, modems, computers and software, to access the Internet in the first place ... cent for Africa; 15 per cent for Latin America and the Caribbean; and 14 per cent for Europe, Central Asia and North America The summary of communications sent and replies received from Governments ... brought together experts and human rights defenders working on a range of Internet and freedom of expression-related issues in order to better understand their experience, needs and priorities in different...
Ngày tải lên: 06/03/2014, 21:20

WORKING PAPER SERIES ON REGIONAL ECONOMIC INTEGRATION NO. 22: India’s Bond Market— Developments and Challenges Ahead docx
... Regulation and Development Agency and provident/pension funds by their own regulator The bankruptcy system is time-consuming and inefficient, although the law is based on United Kingdom law and, ... 6) Ratios in Korea, PRC, and Indonesia were around 150% in 2007; in Malaysia the ratio exceeded 250% and Thailand over 350% (albeit an unusually high figure for Thailand reflecting unusual political ... concludes with a look at the importance of the lessons and innovations of other countries II Development and Outlook: Illiquid and Lagging, but Growing India’s economy has expanded an average...
Ngày tải lên: 22/03/2014, 20:20

Updated Security Considerations for the MD5 Message-Digest and the HMAC-MD5 Algorithms docx
... studied and new cryptographic attacks have been discovered Message digest algorithms are designed to provide collision, pre-image, and second pre-image resistance In addition, message digest algorithms ... Contini, Y.L Yin Forgery and partial key-recovery attacks on HMAC and NMAC using hash collisions ASIACRYPT 2006 LNCS 4284, Springer, 2006 [denBBO1993] den Boer, B and A Bosselaers, "Collisions for ... Krawczyk, H., Bellare, M., and R Canetti, "HMAC: Keyed-Hashing for Message Authentication", RFC 2104, February 1997 [HMAC-MD5] Cheng, P and R Glenn, "Test Cases for HMAC-MD5 and HMAC-SHA-1",...
Ngày tải lên: 29/03/2014, 20:20

Synthesis and optimization of DSP algorithms - 2004
... SYNTHESIS AND OPTIMIZATION OF DSP ALGORITHMS This page intentionally left blank Synthesis and Optimization of DSP Algorithms by George A Constantinides Imperial ... compression, speech recognition and synthesis, digital audio and cameras, mobile telephony, echo cancellation, and even active suspension in the automotive industry In parallel to, and intimately linked ... computational demands of many DSP algorithms continue to outstrip the available computational power As a result, many custom hardware implementations of DSP algorithms are produced - a time consuming and...
Ngày tải lên: 09/04/2014, 16:39

e.r. davies - computer and machine vision. theory algorithms practicalities 4th
... Introduction 185 Dilation and Erosion in Binary Images 186 7.2.1 Dilation and Erosion .186 7.2.2 Cancellation Effects 186 7.2.3 Modified Dilation and Erosion Operators ... Morphological Dilation 187 7.3.2 Generalized Morphological Erosion 188 7.3.3 Duality Between Dilation and Erosion .189 7.3.4 Properties of Dilation and Erosion Operators 190 7.3.5 Closing and Opening ... near-exponential advances and achievements, and witnessed by the quality, and often quantity, of outstanding contributions to the field published in key conferences and journals such as ICCV and PAMI These...
Ngày tải lên: 05/06/2014, 11:45

Báo cáo hóa học: " On relaxed and contraction-proximal point algorithms in hilbert spaces" doc
... article as: Wang and Wang: On relaxed and contraction-proximal point algorithms in hilbert spaces Journal of Inequalities and Applications 2011 2011:41 Submit your manuscript to a journal and benefit ... knowledge that ||en||® and λn 2λn = → 0, ρn 2λn + δn δn δn = → 1, 2ρn 2λn + δn Wang and Wang Journal of Inequalities and Applications 2011, 2011:41 http://www.journalofinequalitiesandapplications.com/content/2011/1/41 ... proximal point algorithms in Hilbert space Taiwan J Math 12, 1691–1705 (2008) Page of Wang and Wang Journal of Inequalities and Applications 2011, 2011:41 http://www.journalofinequalitiesandapplications.com/content/2011/1/41...
Ngày tải lên: 21/06/2014, 00:20

Báo cáo hóa học: " Optimal and Suboptimal Finger Selection Algorithms for MMSE Rake Receivers in Impulse Radio Ultra-Wideband Systems" pdf
... selection algorithms for an IR-UWB system with Nc = 20 and N f = In these simulations, there are five equal energy users in the system (K = 5) and the users’ TH and polarity codes are randomly generated ... components and the taps are exponentially decaying The IR-UWB system has Nc = 20 chips per frame and N f = frame per symbol There are equal energy users in the system and random TH and polarity codes ... networks, wireless communications and geolocation algorithms, network security, and teletraffic and queuing theory He published Modeling and Analysis (Addison-Wesley, 1978), and is authoring a new book...
Ngày tải lên: 22/06/2014, 22:20

DESIGN AND ANALYSIS OF DISTRIBUTED ALGORITHMS phần 2 ppt
... obtained by Kadathur Lakshmanan, N Meenakshi, and Krishnaiyan Thulasiraman [9] and independently by Israel Cidon [4] The difficulty of performing a wake-up in labeled hypercubes and in complete graphs ... currently and frequently used The more sophisticated refinements of adding reply and a convergecast were discussed and employed independently by Adrian Segall [11] and Ephraim Korach, Doron Rotem and ... Max{d(x, z) : z ∈ T [y − x]} is the longest distance between x and the nodes in T [y − x] Let d1 [x] and d2 [x] be the largest and second-largest of all {d[x, y] : y ∈ N (x)}, respectively The centers...
Ngày tải lên: 12/08/2014, 16:21
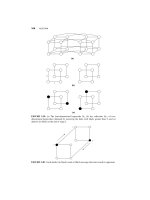
DESIGN AND ANALYSIS OF DISTRIBUTED ALGORITHMS phần 4 docx
... the usual id and stage number In particular, the fields Source and Dest have been described as lists of labels; as we only send compressed paths, Source and Dest contain at most log n labels each ... enters stage i + (and thus both y and z are defeated); it will prepare an election message for the candidates in both directions, say u and v, and will send it directly to y and to z As before, ... In particular, if the link between p and q is labeled d at p, this link is labeled n − d at q Note that the oriented ring is the chordal ring Cn where label corresponds to “right,” and n − to...
Ngày tải lên: 12/08/2014, 16:21

DESIGN AND ANALYSIS OF DISTRIBUTED ALGORITHMS phần 6 potx
... OPERATIONS and Michael Rodeh [21] Nicola Santoro, Jeffrey Sidney, and Stuart Sidney designed Protocol RandomFlipSelect [19] Protocol RandomRandomSelect is due to Nicola Santoro, Michael Scheutzow, and ... developed by Doron Rotem, Nicola Santoro, and Jeffrey Sidney [16], and by Nicola Santoro and Jeffrey Sidney [18] The more efficient protocol Filter was developed by John Marberg and Eli Gafni [11] The ... [6] , and by Alberto Negro, Nicola Santoro, and Jorge Urrutia [12] Selection among two sites was first studied by Michael Rodeh [14]; his solution was later improved by S Mantzaris [10], and by...
Ngày tải lên: 12/08/2014, 16:21

DESIGN AND ANALYSIS OF DISTRIBUTED ALGORITHMS phần 7 docx
... Paola Alimonti, Paola Flocchini, and Nicola Santoro [1] The trade-offs for wake-up in complete graphs with chordal labeling are due to Amos Israeli, Evangelos Kranakis, Danny Krizanc, and Nicola ... Mark Overmars and Nicola Santoro [21] The problem of symmetry breaking was first studied for rings by Alon Itai and Michael Rodeh [14] and for other networks by Doron Rotem and Nicola Santoro [23] ... result If the result of AND is 1, all the entities have value and are in state minimum, and thus know the result If the result of AND MIN-FINDING AND ELECTION: WAITING AND GUESSING 367 is 0, the...
Ngày tải lên: 12/08/2014, 16:21

DESIGN AND ANALYSIS OF DISTRIBUTED ALGORITHMS phần 8 doc
... modeled by declaring one of the two incident nodes to be faulty and to lose all the message to and from its neighbor Similarly, the corruption of a message during transmission must be blamed on one ... entity), and we will treat both spontaneous events and the ringing of the alarm clocks as the same type of events and call them timeouts We represent by (x, M) the event of x receiving message M, and ... restricted environments To understand which properties (and thus restrictions) would suffice we need to examine the proof of Theorem 7.2.1 and to understand what are the particular conditions inside a general...
Ngày tải lên: 12/08/2014, 16:21

DESIGN AND ANALYSIS OF DISTRIBUTED ALGORITHMS phần 9 pdf
... all and only the messages sent by xl are lost Then, for each ⌳ and l, ψ⌳,l ∈ Omit Let configurations A and B be l-adjacent Consider the events ψ⌳(A),l and ψ⌳(B),l for A and B, respectively, and ... predicate (using and, ” “or,” and “p-of-q” connectors) on its outgoing links; examples of such predicates are as follows: “(two of l1 , l2 , l3 ) or ( l1 and l4 )” and “( l1 and l2 ) or ( l3 and l4 ),” ... Danny Dolev and Ray Strong [17] Consensus with Byzantine entities in particular classes of graphs was investigated by Cinthia Dwork, David Peleg, Nick Pippenger, and Eli Upfal [18], and by Pitior...
Ngày tải lên: 12/08/2014, 16:21

DESIGN AND ANALYSIS OF DISTRIBUTED ALGORITHMS phần 10 docx
... if the needed structure and information is in place, a single request for the token can be easily and simply handled, correctly maintaining and updating the structure and information If there ... first observed by Mani Chandy and Leslie Lamport [3] Protocols to construct a consistent snapshot when the links are not FIFO were designed by Ten Lai and Tao Yang [12] and Friedmann Mattern [15]; ... in isolation as different problems, overlooking the similarities and the commonalities and sometimes proposing the same techniques In addition, because of its link with cycle detection and with...
Ngày tải lên: 12/08/2014, 16:21

Báo cáo y học: "Anopheles gambiae genome reannotation through synthesis of ab initio and comparative gene prediction algorithms" pps
... evidence, and the right side is a reverse-color image of, from left to right lanes, PhiX/Lambda DNA size standard (Ph), 250 bp DNA ladder (La) , and PCR performed on either cDNA (cD), or gDNA template ... missing genes [8] On the other hand, due to the lack of comparison with known proteins, ab initio algorithms normally result in over-prediction, and unlike comparative algorithms, they not provide ... Synthesis of comparative and ab initio gene prediction algorithms The GENSCAN, GeneMark and SNAP prediction tools utilizing ab initio algorithms yielded 32,020, 24,579, and 24,451 A gambiae CDSs,...
Ngày tải lên: 14/08/2014, 16:21

nayak - the global financial crisis; genesis, policy response and road ahead (2013)
... stable due to migration of labor and relatively higher labor availability caused by displacement labor from closure of manufacturing in many industries in the USA and EU (European Union) Unprecedented ... high and low unemployment rates which were 7.5 and 2.5% in 1950s were 7.1 and 3.4% in 1960s, went up to and 3.9%, respectively, in 1970s, and to 10.8 and 5% in 1980s The rates declined to 7.8 and ... the labor force, the accumulation of physical and human capital, and advance of technology.… The observed growth paths are not smooth They are punctuated by recessions, large and small, and by...
Ngày tải lên: 01/11/2014, 22:07