list security tools for penetration testing project

AN OVERVIEW OF NETWORK SECURITY ANALYSIS AND PENETRATION TESTING docx
... Concepts of Penetration Testing and Network Security Analysis This section of the document lays down much of the Information Security foundations, documenting the rationale behind Penetration Testing ... by managed security solutions http://www.mis-cds.com Part II, Penetration Testing This section of the book will cover Penetration Testing and the techniques involved when performing testing and ... networks http://www.mis-cds.com Chapter The Equipment and Tools Required to Perform Penetration Testing Determined hackers and Information Security enthusiasts will be knowledgeable in the running...
Ngày tải lên: 05/03/2014, 21:20

Build your own security lab for network testing
... Attack and Penetration Tools Why Attack and Penetration Tools Are Important Vulnerability Assessment Tools Source Code Assessment Tools Application Assessment Tools System Assessment Tools Attributes ... Build Your Own Security Lab Build Your Own Security Lab A Field Guide for Network Testing Michael Gregg Wiley Publishing, Inc Build Your Own Security Lab: A Field Guide for Network Testing Published ... building a hardware test platform Chapter 2, Building a Software Test Platform — Looks at your options for setting up a software test platform You should never be testing a tool for the first time on...
Ngày tải lên: 19/03/2014, 13:32
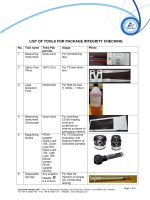
LIST OF TOOLS FOR PACKAGE INTEGRITY CHECKING 15 aug 2012
... LIST OF OTHER TOOLS No Tool name Tetra Pak part No 90337‐0007 Usage Areometer, 27000200 TEST APPARATUS 90298‐0030 For Hydrogen Peroxide residue test (1 ... Any supplier For cutting the package sharply (TS tear down test, Dissolving test, Conductivity test, ) Water tray Any supplier For Conductivity test (with salt solution 1.0%) Pipettes Any supplier For ... Conductivity test (with salt solution 1.0%) Pipettes Any supplier For Red Ink Dye test Photo For Hydrogen Peroxide Concentration check Tetra Pak Vietnam JSC Floor 14, Metrololitan Building,...
Ngày tải lên: 08/09/2016, 08:55

Tài liệu Tools for Security Testing ppt
... ftp://ftp.ox.ac.uk/pub/wordlists/ for a variety of lists including several foreign language lists JTR comes with a number of command-line options you can use to modify its behavior We'll show you the list of the ... Additional Security Tools This is a list (by no means comprehensive) of some additional security tools that may be useful to you These include network scanners and sniffers, traffic capture tools, ... secure kernels and security auditing tools dsniff This suite of packet sniffing tools allows you to monitor traffic on your network for sensitive data It comes with a number of tools including its...
Ngày tải lên: 11/12/2013, 15:15

Tài liệu BackTrack 4: Assuring Security by Penetration Testing pptx
... in VirtualBox Chapter 2: Penetration Testing Methodology Types of penetration testing Black-box testing White-box testing Vulnerability assessment versus penetration testing www.it-ebooks.info ... Assuring Security by Penetration Testing Master the art of penetration testing with BackTrack Shakeel Ali Tedi Heriyanto BIRMINGHAM - MUMBAI www.it-ebooks.info BackTrack 4: Assuring Security by Penetration ... robust penetration testing of your network BackTrack 4: Assuring Security by Penetration Testing is a fully focused, structured book providing guidance on developing practical penetration testing...
Ngày tải lên: 20/02/2014, 11:20

Advanced penetration testing for highly secured environments
... to advanced penetration testing Vulnerability assessments Penetration testing Advanced penetration testing Before testing begins Determining scope Setting limits — nothing lasts forever 8 10 ... Lead for one of the Fortune 500 Among many other responsibilities, he performs security assessments and penetration testing Lee is very passionate and driven about the subject of penetration testing ... Advanced Penetration Testing for Highly-Secured Environments: The Ultimate Security Guide Learn to perform professional penetration testing for highly-secured environments...
Ngày tải lên: 19/03/2014, 13:32

how to cheat at configuring open source security tools - the perfect reference for the multitasked sysadmin
... needs for companies in the many areas of information security He also promotes an inclusive, positive security philosophy for companies, which encourages communicating the merits and reasons for security ... Compute Information Systems, Larry is currently exploring his options for graduate education In addition to his industry experience, Larry is also a Security Evangelist for the PaulDotCom Security ... when searching for security software on the Internet is that it is precisely security software that is most often a security risk Countless Internet sites like to offer up security tools to discover...
Ngày tải lên: 25/03/2014, 11:23

the ethical hack - a framework for business value penetration testing
... Framework for Business Value Penetration Testing OTHER INFORMATION SECURITY BOOKS FROM AUERBACH Asset Protection and Security Management Handbook POA Publishing ISBN: 0-8493-1603-0 Information ... Transmission Security Protocol Security Routing Protocol Security Network Access Controls Service Security Application Security Security Architecture Resource Layer Control Perimeter Extended Chapter Information ... Information Security Management Handbook, 5th Edition Harold F Tipton and Micki Krause ISBN: 0-8493-1997-8 Information Security Policies, Procedures, and Standards: Guidelines for Effective Information...
Ngày tải lên: 25/03/2014, 12:12

monitoring and evaluation tools for biodiversity conservation development projects
... objectives for the project monitoring work Monitoring and evaluation: tools for biodiversity conservation and development projects Exercise: Clarifying the information needs of project staff Project ... qualitative information Depending on your information needs, you might be looking for primary information (new information that you are the first to collect) or secondary information (information ... of information project staff need? Where will they get this information from? How often, and when, is this information required? In what format should the information be made available to project...
Ngày tải lên: 22/05/2014, 12:52

Tools for Project Management, Workshops and Consulting pdf
... Project management Project contract LogFrame Project roadmap/programme Work breakdown structure Gantt chart Project work plan Project environment analysis Project structure Project management ... ‘Andler best-pratice list of tools , a TOP 10 list of the most preferred tools and an overview of project management planning and scoping tools have been added There are 23 new tools in this edition, ... analysis Project WBS Stakeholder map, etc Project activities plan Hypotheses definition Project task list Hypotheses Hypothesis tree Project activities schedule Project environment analysis Gantt project...
Ngày tải lên: 29/06/2014, 08:20

Penetration testing for web applications
... Blackbox Testing Method The blackbox testing method is a technique for hardening and penetration- testing Web applications where the source code to the application is not available to the tester It forces ... the database For more information on PHP/MySQL security issues, refer to http://www.phpadvisory.com PHP/Mysql security issues are on the increase reference phpMyshop (http://www.securityfocus.com/bid/6746) ... of protocols, languages and formats - HTTP, HTTPS, HTML, CSS, JavaScript, etc - that are used as a platform for the construction of Web applications HTTP provides two forms of authentication: Basic...
Ngày tải lên: 14/12/2021, 16:42

offensive security penetration testing with backtrack (lab guide)v3 2
... Offsec FAQ BEFORE connecting to the Labs http://forums.offensive -security. com/forumsdisplay.php?f=69 http://forums.offensive -security. com/forumsdisplay.php?f=84 16 iv Control Panel Once logged into ... broadcast for distance 61 prior written permission from the author system, without -75 OS learning, in any form or by any means such as any information storage, transmission, or retrieval 12 Penetration ... retrieval 12 Penetration Testing with BackTrack A Note from the Authors Thank you for opting to take the “Offensive Security PWB” extended lab training PWB is not your usual IT security course We hope...
Ngày tải lên: 21/08/2014, 14:10

LPTv4 module 29 physical security penetration testing
... Network Penetration Testing Penetration Testing Wireless Network Denial of Service Penetration Testing Penetration Testing IDS Penetration Testing Cont’d Application Penetration Testing EC-Council ... Penetration Testing Roadmap (cont d) (cont’d) Cont’d Physical Security Database Penetration testing P i i VoIP Penetration T i P i Testing War Dialing VPN Penetration Testing Penetration Testing ... Management Penetration Testing Blue Tooth and Hand held Device Penetration Testing File Integrity Checking End Here Data Leakage Penetration Testing EC-Council Security Patches Penetration Testing...
Ngày tải lên: 14/12/2021, 21:15

LPTv4 module 39 email security penetration testing
... Network Penetration Testing Penetration Testing Wireless Network Denial of Service Penetration Testing Penetration Testing IDS Penetration Testing Cont’d Application Penetration Testing EC-Council ... Prohibited Penetration Testing Roadmap (cont d) (cont’d) Cont’d y Physical Security Database Penetration testing VoIP Penetration Testing War Dialing VPN Penetration Testing Penetration Testing Virus ... Management Penetration Testing Blue Tooth and Hand held Device Penetration Testing File Integrity Checking End Here Data Leakage Penetration Testing EC-Council Security Patches Penetration Testing...
Ngày tải lên: 14/12/2021, 21:20

LPTv4 module 40 security patches penetration testing
... Network Penetration Testing Penetration Testing Wireless Network Denial of Service Penetration Testing Penetration Testing IDS Penetration Testing Cont’d Application Penetration Testing EC-Council ... Prohibited Penetration Testing Roadmap (cont d) (cont’d) Cont’d Physical Security Database Penetration testing VoIP Penetration Testing War Dialing VPN Penetration Testing Penetration Testing Virus and ... Management Penetration Testing Blue Tooth and Hand held Device Penetration Testing File Integrity Checking End Here Data Leakage Penetration Testing EC-Council Security Patches Penetration Testing...
Ngày tải lên: 14/12/2021, 21:20

Mastering kali linux for advanced penetration testing
... Mastering Kali Linux for Advanced Penetration Testing A practical guide to testing your network's security with Kali Linux, the preferred choice of penetration testers and hackers ... aims to be the single source for testing a network More information on this can be found at www.oissg.org • NIST SP 800-115, technical guide to information security testing and assessment: Written ... the successor to the BackTrack penetration testing platform which is generally regarded as the de facto standard package of tools used to facilitate penetration testing to secure data and voice...
Ngày tải lên: 23/09/2016, 06:06

wardriving wireless penetration testing
... focuses on how a penetration tester can use these vulnerabilities and the tools to exploit them to perform a penetration test on a target’s WLAN Penetration Testing Before beginning a penetration ... engineering For the last years, he as been dedicated to the information security industry providing: penetration testing, wireless audits, vulnerability assessments, and network security engineering for ... as security consulting, penetration testing and contracting with a wide range of organizations xi 410_WD2e_FM.qxd 10/17/06 10:54 AM Page xii Foreword Contributor Joshua Wright is the senior security...
Ngày tải lên: 01/09/2013, 11:27

Inside words - Tools for teaching academic vocabulary grade 4-12
... strategies similar to those highlighted in Tools for Teaching Content Literacy It also joins the two formats: I blended the quick overview format from Tools with several classrooms examples, as ... them alphabetically so they could be easily found for teaching as well as for discussion in study groups or professional development These are tools for teachers, and the purpose of a tool is to ... 97 SURVIVAL OF THE FITTEST 101 THINK-PAIR-SHARE: COLLABORATE FOR UNDERSTANDING 105 VOCAB-O-GRAM 109 WORD SORT 115 Inside Words: Tools for Teaching Academic Vocabulary, Grades 4-12 by Janet Allen...
Ngày tải lên: 04/09/2013, 16:38

Economic metrics for wind energy projects
... Bolinger for US DOE [11] (check) n.a n.a n.a Partial data; 0.68c€/kWh for the most recent n.a projects; 1.7 c€/kWh for older projects Models of projects economic evaluation 3.1 Economic basics of projects ... When investment projects refer to projects for onshore wind, to determine the time for return on investment of the project is necessary to consider the entries of cash receipts as uniforms (which ... of projects are for specific renewable energy projects Together with other indicators of financial attractiveness of the project is a set of tools that can be used selectively to evaluate and project...
Ngày tải lên: 05/09/2013, 16:30