identification authentication and authorization

Privilege and Authorization
... CHAPTER PRIVILEGE AND AUTHORIZATION User VS Application Logins The topics covered in this chapter relate to various privilege and authorization scenarios handled within SQL Server itself ... as the owner of the table ALTER AUTHORIZATION ON JaviersData TO Javier; GO 106 CHAPTER PRIVILEGE AND AUTHORIZATION As a final note on schemas, there is also a command that can be used to move objects ... supported in future versions of SQL Server, and recommends usage of the EXECUTE AS command instead The EXECUTE AS command can be used by any user, and access to impersonate a given user or server...
Ngày tải lên: 05/10/2013, 08:48

Tài liệu The Practical Guide: Identification, Evaluation, and Treatment of Overweight and Obesity in Adults pdf
... Aerobics Research; and Dr Van S Hubbard, National Institute of Diabetes and Digestive and Kidney Diseases The Practical Guide Identification, Evaluation, and Treatment of Overweight and Obesity in ... Obesity (NAASO) and the National Heart, Lung, and Blood Institute (NHLBI) It is based on the Clinical Guidelines on the Identification, Evaluation, and Treatment of Overweight and Obesity in Adults: ... physical activity, and behavior changes and can be used for assessment, treatment, and followup during weight loss and weight maintenance The relationship between the practitioner and these professionals...
Ngày tải lên: 14/02/2014, 09:20

Tài liệu Obesity guidance on the prevention, identification, assessment and management of overweight and obesity in adults and children ppt
... drinks and confectionery high in added sugars other food and drinks high in fat and sugar, such as some takeaway and fast foods Eat breakfast • Watch the portion size of meals and snacks, and how ... implementing the England and Wales National Service Frameworks for children, young people and maternity services (the Children’s NSFs for England and Wales), and ‘Every child matters’ and similar initiatives ... by 2010 and implementing the Children’s NSFs for England and Wales, the National Healthy Schools Programme (and the Welsh Network of Healthy Schools Schemes), and ‘Every child matters’ and similar...
Ngày tải lên: 21/02/2014, 11:20

Obesity guidance on the prevention, identification, assessment and management of overweight and obesity in adults and children docx
... drinks and confectionery high in added sugars other food and drinks high in fat and sugar, such as some takeaway and fast foods Eat breakfast • Watch the portion size of meals and snacks, and how ... implementing the England and Wales National Service Frameworks for children, young people and maternity services (the Children’s NSFs for England and Wales), and ‘Every child matters’ and similar initiatives ... by 2010 and implementing the Children’s NSFs for England and Wales, the National Healthy Schools Programme (and the Welsh Network of Healthy Schools Schemes), and ‘Every child matters’ and similar...
Ngày tải lên: 22/03/2014, 09:20

Báo cáo " A combination of the identification algorithm and the modal superposition method for feedback active control of incomplete measured systems " doc
... sensors The time delay is taken with 1/500 and 1/800 of total duration time T Some of the controlled results are shown in table and Fig and In Fig and 7, thin and dotted lines are uncontrolled responses ... a so called identification process The process identifying the entire external excitation is presented in [1] and is called the original identification algorithm here The original identification ... c uc (14) The control law using the combination of the identification algorithm and the modal superposition method is described as (13) and (14) Numerical simulation Considering a base excited...
Ngày tải lên: 28/03/2014, 13:20

Báo cáo " A combination of the identification algorithm and the modal superposition method for feedback active control of incomplete measured systems" doc
... sensors The time delay is taken with 1/500 and 1/800 of total duration time T Some of the controlled results are shown in table and Fig and In Fig and 7, thin and dotted lines are uncontrolled responses ... a so called identification process The process identifying the entire external excitation is presented in [1] and is called the original identification algorithm here The original identification ... c uc (14) The control law using the combination of the identification algorithm and the modal superposition method is described as (13) and (14) Numerical simulation Considering a base excited...
Ngày tải lên: 28/03/2014, 13:20

aquarium plants their identification cultivation and ecology - karel rataj
Ngày tải lên: 08/04/2014, 12:50

Advanced Radio Frequency Identification Design and Applications Part 1 ppt
... Tree-based RFID Tag Identification Schemes Nai-Wei Lo and Kuo-Hui Yeh Chapter 15 Design and Implementation of a Multi-protocol UHF RFID Tag Simulation Platform 269 Bo Zhang, Dongkai Yang and Qishan Zhang ... data transmission and reception technique for applications including automatic identification, asset tracking and security surveillance As barcodes and other means of identification and asset tracking ... the RFID protocols and their classification are presented Previously presented works on security and managing hacking attacks on RFID systems are surveyed and new techniques and measures in increasing...
Ngày tải lên: 19/06/2014, 23:20

Advanced Radio Frequency Identification Design and Applications Part 2 potx
... wrap and Teflon sheet between the tag and the aluminum plate The Teflon sheet is hard and its thickness at 0.97mm is very close to the 1mm 26 Advanced Radio Frequency Identification Design and Applications ... Frequency Identification Design and Applications including receiver implementation details, receiver gain, communication protocol specifics and interference generated both within the reader and externally ... output impedance of the tag antenna (Dobkin and Weigand, 2005; Prothro et al., 2006) Nikitin and Rao (December 2006) introduced a new method in describing and measuring the backscattered power from...
Ngày tải lên: 19/06/2014, 23:20

Advanced Radio Frequency Identification Design and Applications Part 3 pptx
... inefficient, and its radiation resistance decreases The challenge is to design small and efficient antennas that have a fractal shape l (a) Initiator (b) Generator Fig Initiator and generator of the standard ... of 900 MHz and 50 Ω reference impedance port as shown in Fig Fig The proposed fractal dipole antenna (P3) (Salama and Quboa, 2008a) 36 Advanced Radio Frequency Identification Design and Applications ... investigated Design and Fabrication of Miniaturized Fractal Antennas for Passive UHF RFID Tags 33 previously (Salama and Quboa, 2008a), which has a scaling factor of r = 1/3 and rotation angles...
Ngày tải lên: 19/06/2014, 23:20

Advanced Radio Frequency Identification Design and Applications Part 4 pot
... intersystem and intra-system interference, as 52 Advanced Radio Frequency Identification Design and Applications it operates in the ISM bands (Industrial Scientific and Medical), free bands Many ... Oct 62 Advanced Radio Frequency Identification Design and Applications K Finkenzeller, RFID Handbook: Fundamentals and Applications in Contactless Smart Cards and Identification, 2nd edition, New ... interest in RFID systems and its applications Operating frequencies including 125 KHz–134 KHz and 140 KHz–148.5 KHz LF band, 13.56 MHz HF band and 868 MHz–960 MHz UHF band were applied to various...
Ngày tải lên: 19/06/2014, 23:20

Advanced Radio Frequency Identification Design and Applications Part 5 pptx
... polarization applications which represents one of the availabilty and usefulness in contrast to the conventional meander-line and meander-slot tags Fig 11 Radiation patterns for 900 MHz Fig 12 AR ... and Propag., pp 95–98, ISBN: 0-7803-7846-6, Columbus, Ohio, June 2003, USA [20] Mosallaei, H & Sarabandi, K (2004) A Compact Ultra-wideband Self-complementary Antennas with Optimal Topology and ... resistance of the small loops; and Rl, the ohmic resistance of the antenna wire XL and XC are the inductive and capacitive reactances, respectively The exact expressions for XL and XC will be discussed...
Ngày tải lên: 19/06/2014, 23:20

Advanced Radio Frequency Identification Design and Applications Part 6 potx
... thickness is T, and the size of the metal plate is M The spacing between the antenna and the metal plate is S The equivalent electric and magnetic currents are I and J, respectively Eθ and Eφ correspond ... antenna parameters D and H are selected such that selfresonance occurs at 315 MHz The tap is attached across the center of the NMHA, and the tap width and tap length are denoted as a and b, respectively ... Figs 5.6(a) and (b) The tap structure is rather simple Wire diameters of 0.8 mm and 0.5 mm are selected for the antenna and the tap, respectively Because the spacing between the antenna and the metal...
Ngày tải lên: 19/06/2014, 23:20
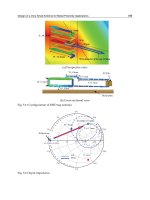
Advanced Radio Frequency Identification Design and Applications Part 7 pdf
... [10] W L Stutzman and G A Thiele, “Antenna Theory and Design, second edition”, John Wiley & Sons, Inc., pp 43-47 and p.71, 1998 [11] W L Stutzman and G A Thiele, “Antenna Theory and Design, second ... Whinnery and Theodore Van Duzer, FIELDS AND WAVES IN COMMUNICATION ELECTRONICS – Third Edition, JOHN WILEY&SONS, INC., pp.189-193, 1993 [18] W L Stutzman and G A Thiele, “Antenna Theory and Design, ... The IC collects power 116 Advanced Radio Frequency Identification Design and Applications and timing information from the electromagnetic field and sends proper backscattered messages to the reader...
Ngày tải lên: 19/06/2014, 23:20
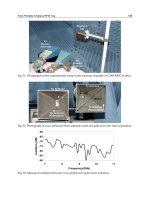
Advanced Radio Frequency Identification Design and Applications Part 9 pot
... Kaklamani, A A Alexandridis, F Lazarakis, K Dangakis (2006), “Circular and elliptical CPW-Fed slot and microstri-fed antennas for ultrawideband applications”, IEEE Antennas and Wireless Propagation ... envelopes and other paper/plastic products, items and documents has been tested successfully The chipless RFID tag operates between and 10.7 GHz of the UWB spectrum By exciting the tag with a wideband ... resonances when performing amplitude and phase data decoding Given the potential high demand on RFID technology in terms of reading range and applications some open issues and further areas of interest...
Ngày tải lên: 19/06/2014, 23:20

Advanced Radio Frequency Identification Design and Applications Part 10 pdf
... k = M( seed T ∗ ), x = P ( k) and seed Ti = M( k) x ← −−−− − send x else choose random number rand calculate s = M( seed Ti ) and m = P ( s ) rand ← −−−− − send rand with probability λ if m = ... and Authentication Protocols for RFID, Proceedings of Pervasive Computing and Communications(PerCom) Workshops, pp 3-12, Mar 2007 Tan, C.; Sheng, B & Li, Q (2008) Secure and Serverless RFID Authentication ... λ = h( f (r j , ti )||n t ) ⊕ idi n t else choose random number rand and n t λ ← −−−− − verify h( f (r j , ti )||n t ) ⊕ idi then send λ = rand n t with the predefined probability Fig 11 Protocol...
Ngày tải lên: 19/06/2014, 23:20

Advanced Radio Frequency Identification Design and Applications Part 11 docx
... the landmarks, and distortion of the terrestrial magnetism Vision-based localization systems suffer from illumination and color changes, bad focused images, image distortions, motion bluer and ... sonic sensor systems and the LRF sensor systems can not detect obstacles or walls, under some surface conditions Second, the RFID systems can handle numerous unique landmarks The landmark is the simplest ... guiding visually impaired Chae and Han (2005) and Kamol et al (2007) used vision information to improve the position estimation performance Zhou et al (2007) and Zhou and Liu (2007) used active RFID...
Ngày tải lên: 19/06/2014, 23:20

Advanced Radio Frequency Identification Design and Applications Part 12 ppt
... pseudorandom tag arrangement exhibit randomness to some extent without increasing the difficulty in installation Fig Random tag arrangement: a) random pattern and b) random arrangement Pseudorandom ... Sensors and Methods for Mobile Robot Positioning, The University of Michigan 220 Advanced Radio Frequency Identification Design and Applications Finkenzeller, K (2000) RFID handbook: Fundamentals and ... the x axis and the y axis A mobile robot is commanded at a constant speed of 10 cm/sec along three linear segments, starting from (30,30), passing through (250,250) and (250,30), and returning...
Ngày tải lên: 19/06/2014, 23:20

Advanced Radio Frequency Identification Design and Applications Part 13 docx
... be on the “underneath” side of the tag and still, be detectable 232 Advanced Radio Frequency Identification Design and Applications The basic behavior and orientation of the magnetic fields ... candidate munitions were considered for tagging The candidates included munitions that were used at firing ranges and that stayed within one meter of the surface when they entered the ground and ... munition 240 Advanced Radio Frequency Identification Design and Applications Evaluation and testing Experimental efforts involved the design, fabrication, and tuning of the custom coil circuits...
Ngày tải lên: 19/06/2014, 23:20

Advanced Radio Frequency Identification Design and Applications Part 14 ppt
... tree-based tag identification protocols such as k-TAS and BS is significant In Fig.7, CM can improve system performance for k-TAS (i=2) scheme between 8% and 9.9% and for BS scheme between 15.3% and 18.3% ... degree in the target identification tree is smaller From Fig.7, CM reduces identification delay for k-TAS (i=2) protocol between 8% and 9.9% and for k-TAS (i=3) between 2% and 4%, respectively ... with Type C and Update of Types A and B, ISO/IEC 18000-6:2004/Amd 1:(E), Jun 2006 [13] D K Klair and K W Chin, “A Novel Anti-Collision Protocol for Energy Efficient Identification and Monitoring...
Ngày tải lên: 19/06/2014, 23:20