database hacking and security

Email hacking and security
... Hacking: EMAIL HACKING AND SECURITY EMAIL HACKING AND SECURITY EMAIL HACKING AND SECURITY EMAIL HACKING AND SECURITY EMAIL HACKING AND SECURITY EMAIL HACKING AND SECURITY EMAIL HACKING AND SECURITY ... EMAIL HACKING AND SECURITY B2: Chọn menu Sniff -> Unified sniffing EMAIL HACKING AND SECURITY B3: Chọn card mạng eth0 -> OK EMAIL HACKING AND SECURITY B4: Chọn menu Hosts -> Scan for hosts EMAIL HACKING ... EMAIL HACKING AND SECURITY B8: Click menu Start -> Start sniffing EMAIL HACKING AND SECURITY Thực Thực hiện trên máy máy Victim: Victim: B1: Mở chương trình Microsoft Live Mail EMAIL HACKING AND SECURITY...
Ngày tải lên: 31/03/2017, 22:46

Ethical Hacking and Countermeasures v6 module 21 physical security
... Ethical Hacking and Countermeasures v6 Physical Security Exam 312-50 Certified Ethical Hacker under medium security take some time to be disengaged, and maximum -security locks are the most complex and ... details of physical security, and advocate measures to strengthen physical security This module will familiarize you with: Security Statistics Physical security Need for physical security Factors ... Hacker Module Flow Security Statistics Physical Security Checklist Mantrap Physical Security Locks Challenges in Ensuring Physical Security Need For Physical Security Wireless Security Spyware...
Ngày tải lên: 26/12/2013, 20:36

Working with Database and Security in Java - Digital Signatures ppsx
Ngày tải lên: 02/08/2014, 08:21

Working with Database and Security in Java - Cryptography (tt) doc
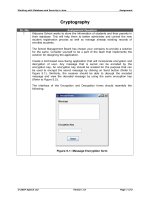
... Working with Database and Security in Java Assignment Figure 5.2: Message Decryption form © 2007 Aptech Ltd Version...
Ngày tải lên: 02/08/2014, 08:21
Working with Database and Security in Java - Cryptography docx
... Working with Database and Security in Java Assignment Figure 5.2: Message Decryption form © 2007 Aptech Ltd Version...
Ngày tải lên: 02/08/2014, 08:21
Working with Database and Security in Java - Java Security doc
Ngày tải lên: 02/08/2014, 08:21

Working with Database and Security in Java - Java Security docx
Ngày tải lên: 02/08/2014, 08:21



User and Security Management
... thành viên vai trò db_owner db_securityadmin: Vai trò cho phép người dùng quản lý tất vai trò thành viên chúng Vai trò cho phép gán quyền hạn cho vai trò Nếu User and Security Management 84 có người ... Database Design and Implementation with SQL Server b c a b c d Database Server 10 Quyền hạn cho phép người dùng xoá tạo lập đối tượng CSDL? Statement permissions User permissions Database permissions ... and Security Management 92 Bài tập Taok lập đăng nhập ‘Frodo’ T-SQL (Gợi ý: Sử dụng thủ tục sp_addlogin ) Tạo lập vai trò ‘Manager’ cho NETDOMAIN thêm thành viên ‘Assistant’ ‘Supervisor’ 93 Database...
Ngày tải lên: 11/09/2012, 13:54


Hands-On Ethical Hacking and Network Defense
... Describe the tools used to attack Web servers Hands-On Ethical Hacking and Network Defense Hands-On Ethical Hacking and Network Defense UNDERSTANDING WEB APPLICATIONS It is nearly impossible to write a program without bugs ... Data stored in a database management system Any system that understands and can issue ODBC commands Interoperability among backend DBMS is a key feature of the ODBC interface 23 OPEN DATABASE CONNECTIVITY ... ODBC defines Standardized representation of data types A library of ODBC functions Standard methods of connecting to and logging on to a DBMS 24 OBJECT LINKING AND EMBEDDING DATABASE (OLE DB)...
Ngày tải lên: 17/09/2012, 10:44

Question Bank Adv .Net and Security in .Net Project
... into a PE file has versioning and an extension of exe permissions [1.5] handles security b) The *.exe file in NET e) All of the above Framework is the same as a standalone executable created by ... ServiceProcessInstaller and ServiceInstaller must be inherited a) Only statements and are d) Statements 1, 2, are true true b) Only statements and are e) None of the above is true true c) Only statements and are ... handler methods used [2.5] for windows services? a) To invoke the methods c) To invoke the methods OnPause() and OnPause() and OnContinue(), the property OnContinue(), the property CanPauseAndContinue...
Ngày tải lên: 09/04/2013, 09:10

Java and Security
... refer to the JDK documentation and the security path of the Java Turorial at http://java.sun.com/docs/books/tutorial /security1 .2/index.html Security Problems and Java Security Testing Finally, the ... comes with the JDK and that provides you with a GUI tool for creating and maintaining policy files keytool—Used to create digital signatures and key pairs and to manage the keystore database jarsigner—Allows ... for testing and not deployed grant { permissionjava .security. AllPermission; }; Security Tools The JDK comes with several tools to help you manage the security of code that you write and wish to...
Ngày tải lên: 29/09/2013, 08:20

Oracle Database Backup and Recovery Advanced User’s Guide
... command to back up database files and archived redo logs Chapter 17, "Performing User-Managed Database Flashback and Recovery" This chapter describes how to use the SQL*Plus FLASHBACK DATABASE and ... primary database that is updated using archived logs created by the primary database RMAN can create or back up a standby database You can fail over to the standby database if the primary database ... to the Target Database and Recovery Catalog from the Command Line 5-3 vi Connecting to the Target Database and Recovery Catalog from the RMAN Prompt Connecting to an Auxiliary Database ...
Ngày tải lên: 16/10/2013, 11:15

Oracle Database Backup and Recovery Basics
... Copies and Backup Sets Full and Incremental Datafile Backups RMAN Backups and Tags Backing Up Database Files and Archived Logs with RMAN Making Consistent and ... Recovery Database Restore and Recovery with RMAN: Overview Scope and Limitations of this Chapter Restore and Recovery with Enterprise Manager Preparing and Planning Database ... for database administrators who perform backup and recovery of an Oracle database server To use this document, you need to know the following: s s Relational database concepts and basic database...
Ngày tải lên: 18/10/2013, 17:15

Apress - Pro SQL Server 2008 Relational Database Design and Implementation (2008)01
... Relational Database Design and Implementation Louis Davidson With Kevin Kline, Scott Klein, and Kurt Windisch 8662FM.qxp 7/28/08 6:19 PM Page ii Pro SQL Server 2008 Relational Database Design and Implementation ... Data Structures Database and Schema Tables, Rows, and Columns The Information ... to the Data 385 Principals and Securables 387 Database Security Overview ...
Ngày tải lên: 29/10/2013, 15:15

Apress - Pro SQL Server 2008 Relational Database Design and Implementation (2008)02
... on database design Louis’s primary areas of interest are database architecture and coding in T-SQL, and he has experience designing many databases and writing thousands of stored procedures and ... Server 2005 Database Design and Optimization (Apress, 2006), and Database Benchmarking: Practical Methods for Oracle & SQL Server (Rampant, 2007) Kevin contributes to SQL Server Magazine and Database ... times, we’ll discuss, debate, and celebrate the topic of database design and how critical it is for any datacentric application Database design is part science and part art There’s a science...
Ngày tải lên: 29/10/2013, 15:15

Apress - Pro SQL Server 2008 Relational Database Design and Implementation (2008)03
... Structures This section introduces the following core relational database structures and concepts: • Database and schema • Tables, rows, and columns • The Information Principle • Keys • Missing values ... the objects in your database as far as is possible It consists of a standard set of views used to view the system metadata and should exist on all database servers of any brand • In the SQL Server–specific ... data and the cleansing inside the database using SQL commands Purpose of Keys Every table should have at least one candidate key—an attribute (or combination of attributes) that can uniquely and...
Ngày tải lên: 08/11/2013, 21:15