access control security systems south africa




The impact of and responses to HIV/AIDS in the private security and legal services industry in South Africa potx
Ngày tải lên: 22/03/2014, 18:20

implementing nap & nac security technologies - the complete guide to network access control
Ngày tải lên: 25/03/2014, 11:44

Research and Training Strategies for Goat Production Systems in South Africa pptx
Ngày tải lên: 31/03/2014, 22:20

Báo cáo y học: "Health system weaknesses constrain access to PMTCT and maternal HIV services in South Africa: a qualitative enquiry" pptx
Ngày tải lên: 10/08/2014, 05:22

Access Control List - ACL
... 2: Router2(config) #access- list 1 deny 42.35.2.18 0.0.0.0 Router2(config) #access- list 1 permit any o Cách 3: Router2(config) #access- list 1 deny 42.35.2.18 Router2(config) #access- list 1 permit any ã Bc 10: t access- list ... một access- list chỉ chận địa chỉ IP 42.35.2.18 kèm theo lệnh access- list 1 permit any. Có 3 cách để thực hiện: o Cách 1: Router2(config) #access- list 1 deny host 42.35.2.18 Router2(config) #access- list ... cần thực hiện là “IP access- group 1 in”. Router2(config)#interface ethernet0 Router2(config-if)#ip access- group 1 in Router2(config-if)#exit 3 d. Kim nh li cỏc Standard Access List ã Bc 11:...
Ngày tải lên: 18/09/2012, 14:04

The Volatility of Capital Flows in South Africa: Some Empirical Observations
... 2 - The Volatility of Capital Flows in South Africa: Some Empirical Observations I. SUMMARY AND CONCLUSIONS In the past several years, South Africa has taken a number of steps, such as ... Jonsson (2001), “The Risk Premium in South African Long-Term Interest Rates,” IMF, mimeo.” 2 This study identified other important determinants of South Africa s risk spreads. These included ... in South Africa have helped reduce the vulnerability of the economy to adverse external shocks and contagion from other emerging markets. The public finances have been brought firmly under control, ...
Ngày tải lên: 24/10/2012, 09:11

Economic viability of a residential building integrated photovoltaic generator in South Africa
Ngày tải lên: 05/09/2013, 16:10

Access Control Lists
... Copyright 2003, Cisco Systems, Inc. Case Study: Access Control Lists (ACLs) 1-15 To help with the physical layer design the company has ... Signature:_________________________Date:_______________ Copyright 2003, Cisco Systems, Inc. Case Study: Access Control Lists (ACLs) 1-9 For the demonstration, the company agrees that it is ... appropriate format ■ Provide a written final report Copyright 2003, Cisco Systems, Inc. Case Study: Access Control Lists (ACLs) 1-13 VLAN Port Assignments Update the switch tables, located...
Ngày tải lên: 16/10/2013, 20:15

Danh sách điều khiển truy cập (Access Control List)
... source 7.4.3.2 Lệnh ip access- group Lệnh này dùng để liên kết một danh sách truy cập đã tồn tại vào một giao diện. Cú pháp như sau: ip access- group access- list-No {in/out} o access- list-no: số ... đề tổng quát, cú pháp được mô tả như sau: access- list access- list- number {permit|deny} {test conditions} o access- list: là từ khóa bắt buộc o access- list-number: Lệnh tổng thể này dùng để ... giao diện. Cú pháp như sau: {protocol} access- group access- list-number Với: Protocol: là giao thức áp dụng danh sách truy cập Access- group: là từ khóa Access- list-number: Số hiệu nhận dạng...
Ngày tải lên: 19/10/2013, 00:20

Access control list
... lệnh: Router(config) #access- list access- list-number {deny | permit} source [ source-wildcard ] ……………… Router(config-if)#{protocol} access- group access- list-number {in | out} Hủy một ACL: Router(config)#no access- list access- list-number ... 0.0.0.0 eq 21 Config# access- list 100 permit IP any any Config#int s0 Config-if# ip access- group 100 IN 192.168.0.18 should be denied website of 192.168.0.34 On Router R3 Config# Access- list 100 deny ... access- list access- list-number 381 CHƯƠNG 7 407 Danh sách kiểm tra truy cập (ACL) Tạo ACL mở rộng S0 S0 E0 E0 A B 192.168.0.34 should be denied FTP of 192.168.0.18 On Router R1 Config# Access- list...
Ngày tải lên: 19/10/2013, 02:20

Basic Access Control
... encrypted. Basic Access Control Security Checklist ã Secure physical access to the router. (See Appendix B). ã Secure console access with the login and password commands. ã Disable or secure AUX access ... methods for access are the lines— console port, auxiliary port, and virtual TTYs. Additional methods include HTTP, TFTP, and SNMP access, and each method of access requires its own access control configuration. Console ... rebooted. Privileged-level access control Once a user is logged into a line with user-level access, he can use the enable com- mand to attempt to gain privilege access. Privilege access allows a user...
Ngày tải lên: 27/10/2013, 07:15

Industrialisation and race in South Africa, 1886–1994
... colonising society. South Africa was reentering the mainstream of African history. P1: RNK 0521864381c12 CUNY780B-African 978 0 521 68297 8 May 15, 2007 16:38 Industrialisation and race in South Africa 281 in ... P1: RNK 0521864381c12 CUNY780B-African 978 0 521 68297 8 May 15, 2007 16:38 Industrialisation and race in South Africa 275 14.Industrialisation and race in South Africa. of 1913 had this objective, ... farm labourers. South Africa suddenly became a relatively high-wage economy for Africans in modern employment, by comparison with other developing coun- tries. This added to the difficulty ofexporting SouthAfrican...
Ngày tải lên: 01/11/2013, 07:20

Interpreting South Africa to Britain – Olive Schreiner, Boers, and Africans
... political goal for South Africa – reconciling Briton and Boer. Nevertheless, Schreiner as a South African is incapable of discussing the future of South Africa without considering Africans. She sees ... white South Africa because she thinks of the British and Boer ‘‘races’’ in social Darwinist terms. Africans cannot be part of the South African of the future; Schreiner’s writings on South Africa ... means that she can posit a future in which Africans remain important for South Africa but not as South Africans. They will do the manual labor for the future South African, who is white. And they will...
Ngày tải lên: 01/11/2013, 08:20

Tài liệu AAA Access Control ppt
... Associates, Inc. All rights reserved. AAA Security Checklist | 51 Token-Based Access Control An authentication method that offers additional security is token-based access con- trol. With this method, ... use smart cards or token-based access control. A word of warning, however: due to the way that HTTP performs authentication, token-based access control cannot be used. AAA Security Checklist This checklist ... additional security by requiring an attacker to both guess the user’s password and steal the smart card or token that is used to access the system. Cisco routers don’t support token-based access control...
Ngày tải lên: 11/12/2013, 13:15
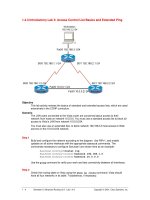
Tài liệu Access Control List Basics and Extended Ping ppt
... v2.0 - Lab 1.4.3 Copyright 2001, Cisco Systems, Inc. Access Control List Basics Access Control Lists (ACLs) are simple but powerful tools. When the access list is configured, each statement ... standard and extended access lists: Two-step process. First, the access list is created with one or more access- list commands while in global configuration mode. Second, the access list is applied ... list. It is not possible to reorder an access list, skip statements, edit statements, or delete statements from a numbered access list. With numbered access lists, any attempt to delete a single...
Ngày tải lên: 21/12/2013, 19:15

Tài liệu Access Control List Basics and Extended Ping doc
... v2.0 - Lab 1.4.3 Copyright 2001, Cisco Systems, Inc. Access Control List Basics Access Control Lists (ACLs) are simple but powerful tools. When the access list is configured, each statement ... standard and extended access lists: Two-step process. First, the access list is created with one or more access- list commands while in global configuration mode. Second, the access list is applied ... this step, you will configure an extended ACL to block access to a Web server. Before you proceed, issue the no access- list 50 and no ip access- group 50 commands on the Vista router to remove...
Ngày tải lên: 21/12/2013, 19:15