access control and security systems jobs

Tài liệu IP Video Security Guide: Global Leaders in Video and Security Systems pptx
... limitations in throughput and search times that cannot sustain video security systems. In reality DVRs and NVRs are primarily very specialized storage systems that can record and replay the vast ... of security. Impact on Network Performance 6.1 IP Video Security Guide Global Leaders in Video and Security Systems Impact on Network Performance 6.0 It is critical to understand ... Control and Conguration 13.0 Camera Control (PTZ) IP cameras can be mounted with a fixed field of view or on motorized platforms that will accept commands for positioning the camera and controlling...
Ngày tải lên: 14/02/2014, 08:20
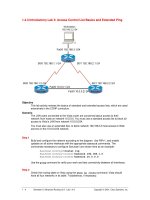
Tài liệu Access Control List Basics and Extended Ping ppt
... to both standard and extended access lists: Two-step process. First, the access list is created with one or more access- list commands while in global configuration mode. Second, the access list ... v2.0 - Lab 1.4.3 Copyright 2001, Cisco Systems, Inc. Access Control List Basics Access Control Lists (ACLs) are simple but powerful tools. When the access list is configured, each statement ... for. The deny command discards packets matching the criteria on that line. Two important keywords that can be used with IP addresses and the access list command are any and host. The keyword...
Ngày tải lên: 21/12/2013, 19:15

Tài liệu Access Control List Basics and Extended Ping doc
... to both standard and extended access lists: Two-step process. First, the access list is created with one or more access- list commands while in global configuration mode. Second, the access list ... v2.0 - Lab 1.4.3 Copyright 2001, Cisco Systems, Inc. Access Control List Basics Access Control Lists (ACLs) are simple but powerful tools. When the access list is configured, each statement ... you will configure an extended ACL to block access to a Web server. Before you proceed, issue the no access- list 50 and no ip access- group 50 commands on the Vista router to remove the ACL...
Ngày tải lên: 21/12/2013, 19:15

Control and scheduling codesign flexible resource management in real time control systems feng xia you xian sun
Ngày tải lên: 01/01/2014, 18:47

Tài liệu Systems Administration and Security ppt
... file, and add nouser=mj. B. Edit the /etc/hosts.deny file and add in.ftpd : user=mj. C. Edit the /etc/ftphosts file and add the user ID for mj to the list. D. Edit the /etc/ftpaccess file and add ... how control flags work, take a look at the /etc/pam.d/reboot configuration file. The first auth command checks the pam_rootok.so module. If the root user runs the reboot command, and the control_ flag ... network or systems security staff, most of the administrators are probably responsible for other operating systems; you’re probably responsible for security policies on your Linux systems. You...
Ngày tải lên: 24/01/2014, 14:20

Sap Solutions For Governance Risk And Compliance And Grc Access Control 3 doc
... Audit Access Controls SAP GRC Access Control © SAP AG 2007, SAP Skills 2007 Conference / G3 / 37 SAP GRC Access Control 5.3 SAP GRC Access Control branding and single launchpad for all 4 access control ... Process Control: Centralized Control Management Centralized Control Management One system for managing automated and manual controls System can manage – Financial Control – Operational Controls – ... Access Control Role Reduce cost of role maintenance Ease compliance and avoid authorization risk Eliminate errors and enforce best practices Assure audit-ready traceability and security...
Ngày tải lên: 05/03/2014, 19:20

BYPASSING NETWORK ACCESS CONTROL SYSTEMS potx
... NAC Systems Abstract The threat of viruses, worms, information theft and lack of control of the IT infrastructure has lead companies to implement security solutions to control the access ... IT operations, network security and regulation compliance. By providing comprehensive network visibility and access control, Insightix customers reduce the time, cost and complexity associated ... elements and users to connect to the network. This set of technologies is termed by many as Network Access Control (NAC) - a set of technologies and defined processes aimed at controlling access...
Ngày tải lên: 14/03/2014, 20:20

implementing nap & nac security technologies - the complete guide to network access control
... Authorized Access and Malicious Use 105 Exploitation by Authorized Physical Access and Unauthorized LAN Access 110 Exploitation with Unauthorized Physical Access and Unauthorized LAN Access 112 Exploitation ... technologies, and standards, the entire market is extremely difficult to understand and comprehend. This confusion leads to many misconceptions and, frankly, many people take bits and pieces of ... and meet your minimum security standards. For example, my gun is unloaded and the blade of my knife is less than 4 inches in length.’’ (He’s lying, and is giving the incorrect state of this security posture....
Ngày tải lên: 25/03/2014, 11:44

information resource guide computer internet and network systems security
Ngày tải lên: 21/04/2014, 14:23

integrated security systems design concepts specifications and implementation jan 2007 ebook ling
... making alarm and access control systems (you read that correctly). What they were actually making was programmable logic controllers (PLCs), which were equipped with an alarm and access control sys- tem ... of network technology and trying to hold tenaciously to controller- based systems. Enter the fifth generation. FIFTH-GENERATION TECHNOLOGY The problem with alarm and access control systems was that their ... became the basis for a new breed of alarm and access control system technology called distributed controller systems. Until 1974, each alarm and access control field device was wired individually...
Ngày tải lên: 04/06/2014, 13:16

Báo cáo hóa học: " Inconsistency resolving of safety and utility in access control" potx
... Cuppens, A stratification-based approach for handling conflicts in access control, in Proceedings of the 8th Symposium on Access Control Models and Technologies, (Villa Gallia, Como, Italy), ... Open Access Inconsistency resolving of safety and utility in access control Jianfeng Lu 1* , Ruixuan Li 2 , Jinwei Hu 3 and Dewu Xu 1 Abstract Policy inconsistencies may arise between safety and ... effectiveness and efficiency of our approach. Keywords: access control, safety, utility, separation- of-duty 1. Introduction The safety and utility policies are very important in an access control...
Ngày tải lên: 20/06/2014, 22:20

Báo cáo hóa học: " Inconsistency resolving of safety and utility in access control" docx
... of access control system environments. Policy inconsistencies may arise between safety and utility policies due to their opposite objectives. And in many cases, it is desirable for access control ... specify reasonable access control policies when b oth safety and utility policies coexists. 6. Conclusion and future work In this paper, we handled policy inconsistency of safety and utility policies ... effectiveness and efficiency of our approach. Keywords: access control, safety, utility, separation- of-duty 1. Introduction The safety and utility policies are very important in an access control...
Ngày tải lên: 21/06/2014, 00:20

Báo cáo hóa học: " Research Article AWPP: A New Scheme for Wireless Access Control Proportional to Traffic Priority and Rate" pdf
... Technology—Telecommunications and information exchange between systems- Local and metropolitan area net- works-Specific requirements—part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) ... 802.11e WG, IEEE Standard for Information Tech- nology—Telecommunications and Information Exchange Between Systems LAN/MAN Specific Requirements—part 11 Wireless Medium Access Control and Physical Layer specifications, ... Standard for Information Technology—Telecommunications and Information Exchange between systems- Local and metropolitan area networks-Specific Requirements—part 11:Wireless LAN Medium Access Control...
Ngày tải lên: 21/06/2014, 05:20

Báo cáo hóa học: "Research Article Admission Control and Interference Management in Dynamic Spectrum Access Networks" pot
... results obtained for systems 3a and 4. Recall that systems 3a and 5a do not support SH, deploy CAP but no repacking, while systems 4 and 5b do support SH, deploy CAP and repacking. However, S5a and S5b deploy ... Recall that system 2 (S2) deploys the conventional random channel allocation algorithm, while systems 3a (S3a) and 4 (S4) deploy CAP and CAP and repacking (CAP+RP), respectively. To highlight the ... to the random access case. Finally, we proposed and evaluated a novel adaptive admissioncontrolschemeforSUsthatisabletolimit simultaneously the probability of forced termination of SUs and the...
Ngày tải lên: 21/06/2014, 17:20

ROBOTIC SYSTEMS – APPLICATIONS, CONTROL AND PROGRAMMING doc
... Therefore, we address the issue of Robotic Systems – Applications, Control and Programming 16 0 5 10 15 Mental Demand Physical Demand Te mp or al Demand Performance Effort Frustration Topology ... high density control board was designed and developed in-house. This control board consisted of one CC2430 microcontroller (Texas Instrument, USA) as the main wireless controller and three sets ... Annika Raatz and Thomas Vietor Part 3 Vision and Sensors 411 Chapter 20 Real-Time Robotic Hand Control Using Hand Gestures 413 Jagdish Lal Raheja, Radhey Shyam, G. Arun Rajsekhar and P. Bhanu...
Ngày tải lên: 27/06/2014, 06:20

ROBOTIC SYSTEMS – APPLICATIONS, CONTROL AND PROGRAMMING potx
... high density control board was designed and developed in-house. This control board consisted of one CC2430 microcontroller (Texas Instrument, USA) as the main wireless controller and three sets ... orders@intechweb.org Robotic Systems – Applications, Control and Programming, Edited by Ashish Dutta p. cm. ISBN 978-953-307-941-7 Robotic Systems – Applications, Control and Programming 22 presented ... line) and the reconfigurable master device (bottom line): one module (left), assembled modules (middle) and prototypes (right) Robotic Systems – Applications, Control and Programming...
Ngày tải lên: 29/06/2014, 09:20

New Trends in Technologies: Control, Management, Computational Intelligence and Network Systems pdf
Ngày tải lên: 29/06/2014, 14:20


Bạn có muốn tìm thêm với từ khóa: