Information Security FUNDAMENTALS phần 2 doc

Information Security FUNDAMENTALS phần 2 doc
... September 10, 20 04 5:46 PM Copyright 20 05 by CRC Press, LLC. All Rights Reserved. Chapter 2 Threats to Information Security 2. 1 What Is Information Security? Information security is ... of information security is the security policy (see Figure 2. 1). If information security were a person, the security policy would be the central nervous system. Policies...
Ngày tải lên: 14/08/2014, 18:22

Information Security FUNDAMENTALS phần 7 docx
... Cipher ï Block Ciphers DB1 DB2 DB3 DB4 CT1 CT2 CT3 CT4 Data Block 1 Data Block 2 Data Block 3 Data Block 4 AU1957_C006.fm Page 160 Monday, September 20 , 20 04 3 :23 PM Copyright 20 05 by CRC Press, LLC. ... September 10, 20 04 5:46 PM Copyright 20 05 by CRC Press, LLC. All Rights Reserved. FIGURE 6 .2 Spoofing Hardware AU1957_C006.fm Page 147 Monday, September 20 , 20 04 3 :23 P...
Ngày tải lên: 14/08/2014, 18:22
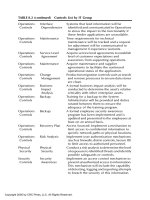
Information Security FUNDAMENTALS phần 9 docx
... Preventive Control Information Preventive Control Data Sought Interview Subjects Information security Information security policies, standards, and procedures Information security management, ... Ⅲ Information security controls Ⅲ Environmental security Ⅲ Physical security Ⅲ Disaster recovery plans (i.e., existing plans to recovery IT capabilities) Ⅲ...
Ngày tải lên: 14/08/2014, 18:22

Network Security Foundations phần 2 docx
... a security concern. Many organizations allow employees to remotely access their computers from home using this method. 4374Book.fm Page 25 Tuesday, August 10, 20 04 10:46 AM 22 Chapter 2 ... example, if a message says it’s 24 0 bytes long but it’s actually 25 6 bytes long, the receiving service may allocate a buffer only 24 0 bytes long but then copy 25 6 bytes of informa...
Ngày tải lên: 13/08/2014, 15:21

Information Security FUNDAMENTALS phần 1 pps
... Typical Information Protection Program 1.8 Summary Chapter 2 Threats to Information Security 2. 1 What Is Information Security? 2. 2 Common Threats 2. 2.1 Errors and Omissions 2. 2 .2 Fraud ... Theft 2. 2.3 Malicious Hackers 2. 2.4 Malicious Code 2. 2.5 Denial-of-Service Attacks 2. 2.6 Social Engineering 2. 2.7 Common Types of Social Engineering 2. 3 Summary Chapter...
Ngày tải lên: 14/08/2014, 18:22

Information Security FUNDAMENTALS phần 3 pptx
... plus messages on: Ⅲ Information security standards Ⅲ Information security monitoring Ⅲ Information security performance measurement Ⅲ More information security good practices Of ... on: Ⅲ Information security policies Ⅲ Information ownership Ⅲ Information classification Ⅲ Good information security practices Because employee information s...
Ngày tải lên: 14/08/2014, 18:22

Information Security FUNDAMENTALS phần 4 pps
... Groups Corporate Committees (IS Steering Committee) (4.1 .2, 4.1.7, 12. 2.1, 12. 2 .2, 12. 3.1) ISO Sections (3.1.1, 4.1.1, 4.1.4, 11.1 .2, 12. 2.1) Copyright 20 05 by CRC Press, LLC. All Rights Reserved. 4.8.4 ... Friday, September 10, 20 04 5:46 PM Copyright 20 05 by CRC Press, LLC. All Rights Reserved. When creating an Information Security Policies and Standards document, each sec...
Ngày tải lên: 14/08/2014, 18:22

Information Security FUNDAMENTALS phần 5 ppt
... 1, 2, and 3 Information Security Tier 1 Personnel Security Tier 2 Job Descriptions User Training Security Incidents Tier 3 AU1957_book.fm Page 98 Friday, September 10, 20 04 5:46 PM Copyright 20 05 ... concept TABLE 5 .2 Criticality Matrix Business Impact Classification Level Maximum 1 2 3 Medium 2 2 3 Minimum 2 3 4 1: Availability safeguards must be implemented....
Ngày tải lên: 14/08/2014, 18:22

Information Security FUNDAMENTALS phần 6 ppt
... Monday, September 20 , 20 04 3 :23 PM Copyright 20 05 by CRC Press, LLC. All Rights Reserved. TABLE 5.8 Information Classification Policy: Example 3 INFORMATION CLASSIFICATION Introduction Information, ... social security number, etc.), Ⅲ Vendor information (name, address, product pricing specific to the com- pany, etc.), AU1957_book.fm Page 122 Friday, September 10, 20 04 5:46 PM...
Ngày tải lên: 14/08/2014, 18:22

Information Security FUNDAMENTALS phần 8 ppt
... safeguards, and processes that are FIGURE 8 .2 Information Security Life Cycle AU1957_book.fm Page 186 Friday, September 10, 20 04 5:46 PM Copyright 20 05 by CRC Press, LLC. All Rights Reserved. ... Disposal of Documents While security precautions and fire prevention and suppression systems can ensure the safety of information within data centers, often little is done to prot...
Ngày tải lên: 14/08/2014, 18:22