security assessment case studies for implementing the nsa iam phần 9 pot

security assessment case studies for implementing the nsa iam phần 9 pot
... conduct the assessment. In our case, we describe the NSA IAM as the methodology used to conduct the assessment and the basis for the assessment process. Since this is the main document, the assessment ... anal- ysis. Security Horizon utilized the National Security Agency (NSA) Information Security Assessment Methodology (IAM) to conduct the organizati...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 4 pot
... the columns across the top of the matrix with the names of the impact attributes we’ll be using for the assessment. The rows are labeled along the left edge with the information types that the customer ... information or systems should be protected and why. NSA has decided that for these reasons, it makes the most sense for the assessment team to act in the...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 5 potx
... up the TAP, since it can be considered the core outcome of the pre -assessment site visit .The TAP is the primary deliverable created during the pre -assessment phase .The TAP combines all the information ... extension of the boundaries resulted in exceptionally long days for the assessment team. The assessment was completed, but it took extra effort on the part...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 10 pot
... meeting, 310–312 audit assessment vs., 54–56 as impact attribute, 98 for INFOSEC, 240 request for IAM prior to, 59 authentication, 237–238 authorization, 98 availability, 94 , 95 , 96 97 B biometrics, ... findings, 3 39 340 critical information topics, 86 93 critical path, 132 286 _NSA_ IAM_ Index.qxd 12/17/03 10:31 AM Page 418 422 Index defined, 94 definitions, creating,...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 1 docx
... drive the assessment effort. Ultimately, the majority of information is the same in either www.syngress.com Laying the Foundation for Your Assessment • Chapter 1 3 Contracting and the NSA IAM NSA ... of performing assessments the way NSA does. To recap, the IAM trains the individuals in the IAM standard, while the IA- CMM appraises the organization’s ab...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 2 ppt
... directly from the integration of the organization’s mission with the IAM process and security www.syngress.com 46 Chapter 2 • The Pre -Assessment Visit Figure 2.1 The IAM Timeline: The Pre -Assessment ... phases of the IAM assessment. This allows the assessment plan to be used as the scoping input for the onsite assessment contract. Understanding Scoping...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 3 ppt
... have the appropriate pieces in place to create the OICM.This is one of the primary deliverables of the IAM assessment; it defines much of the key information that lays the foundation for the remainder ... the time the IAM engagement gets into full swing, however, the main customer POC is often the biggest proponent of the process. Who Is the Assessment Team L...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 6 pdf
... flow for the process .The customer should be presented with the assessment s ultimate objec- tives as defined by the customer during the pre -assessment phase. Keeping these objectives in the forefront ... the customer and the assessment team. Continued Customer Education The education process for the customer doesn’t stop at the pre -assessment phase or even the...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 7 doc
... questions that will help the assessment team gain the needed information and identify the organization’s vulnerabilities .The first resource for questions comes from the security expertise of the assessment ... feedback from the departments that the assessment was going better than they expected and that they found value in the information that was being collected.Th...
Ngày tải lên: 13/08/2014, 15:21
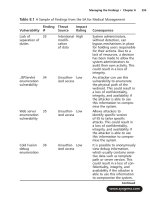
security assessment case studies for implementing the nsa iam phần 8 docx
... have to map the finding to the OICM, or can you just map it to the SICM? A: As you have already learned, the impact definitions are the same for both the OICM and the SICM.Therefore, the findings ... client.They are now all on the same page when it comes to their critical systems and critical information.They are all aware of the issues or vulnerabilities they have within t...
Ngày tải lên: 13/08/2014, 15:21