security assessment case studies for implementing the nsa iam phần 8 docx
security assessment case studies for implementing the nsa iam phần 8 docx
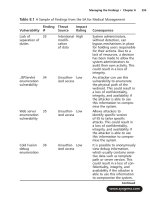
... click on the “Ask the Author” form. You will also gain access to thousands of other FAQs at ITFAQnet.com. 286 _NSA_ IAM_ 08. qxd 12/15/03 5:03 PM Page 307 286 _NSA_ IAM_ 09.qxd 12/16/03 12: 58 PM Page ... have to map the finding to the OICM, or can you just map it to the SICM? A: As you have already learned, the impact definitions are the same for both the OICM and the...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 1 docx
... Posture 282 The Yugo Implementation 283 The Ford Solution 284 The Cadillac Solution 284 Case Study: Medical Management 284 System Description 286 Information Criticality 286 Summary of Findings 287 Excerpt ... drive the assessment effort. Ultimately, the majority of information is the same in either www.syngress.com Laying the Foundation for Your Assessment • Chapter...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 2 ppt
... team. www.syngress.com 38 Chapter 1 • Laying the Foundation for Your Assessment 286 _NSA_ IAM_ 01.qxd 12/15/03 3:15 PM Page 38 Introduction The Pre -Assessment site visit supports multiple aspects of the NSA INFOSEC Assurance ... directly from the integration of the organization’s mission with the IAM process and security www.syngress.com 46 Chapter 2 • The Pre -A...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 3 ppt
... types. www.syngress.com 88 Chapter 3 • Determining the Organization’s Information Criticality 286 _NSA_ IAM_ 03.qxd 12/11/03 3:25 PM Page 88 Planning for the Assessment Activities The amount of work ... have the appropriate pieces in place to create the OICM.This is one of the primary deliverables of the IAM assessment; it defines much of the key information that la...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 4 pot
... the columns across the top of the matrix with the names of the impact attributes we’ll be using for the assessment. The rows are labeled along the left edge with the information types that the customer ... information or systems should be protected and why. NSA has decided that for these reasons, it makes the most sense for the assessment team to act in the...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 5 potx
... up the TAP, since it can be considered the core outcome of the pre -assessment site visit .The TAP is the primary deliverable created during the pre -assessment phase .The TAP combines all the information ... extra effort on the part of the assessment team to define the new boundaries and wasted valuable resources during the onsite phase. 286 _NSA_ IAM_ 05.qxd 12/11...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 6 pdf
... flow for the process .The customer should be presented with the assessment s ultimate objec- tives as defined by the customer during the pre -assessment phase. Keeping these objectives in the forefront ... the customer and the assessment team. Continued Customer Education The education process for the customer doesn’t stop at the pre -assessment phase or even the...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 7 doc
... low www.syngress.com Managing the Findings • Chapter 8 283 286 _NSA_ IAM_ 08. qxd 12/15/03 5:03 PM Page 283 NOTE The assessment team utilized NSA s 18 Baseline INFOSEC Classes and Categories as the high-level guide for conducting ... every www.syngress.com 282 Chapter 8 • Managing the Findings 286 _NSA_ IAM_ 08. qxd 12/15/03 5:03 PM Page 282 Best Practices Checklist...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 9 pot
... conduct the assessment. In our case, we describe the NSA IAM as the methodology used to conduct the assessment and the basis for the assessment process. Since this is the main document, the assessment ... anal- ysis. Security Horizon utilized the National Security Agency (NSA) Information Security Assessment Methodology (IAM) to conduct the organizati...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 10 pot
... meeting, 321–322 sources for assessment work, 7 timeline form, 414–415 See also National Security Agency (NSA) Information Security (INFOSEC) Assessment Methodology (IAM) assessment plan attached ... information criticality; system information criticality information exchange, 231–232 information request, 69–70 Information Security (INFOSEC) assessment, 6, 23 documentation, 23...
Ngày tải lên: 13/08/2014, 15:21
- the complete guide to the toefl ibt part 8 docx
- tournament incentives for teachers the case of chile
- case studies in finance managing for corporate value solutions
- the distance education evolution issues and case studies
- report of the food security assessment west bank and gaza strip
- implementing ssh strategies for optimizing the secure shell pdf