security assessment case studies for implementing the nsa iam phần 5 potx

security assessment case studies for implementing the nsa iam phần 5 potx
... of that information later in our team discussion. www.syngress.com The System Security Environment • Chapter 5 1 75 286 _NSA_ IAM_ 05. qxd 12/11/03 3:28 PM Page 1 75 ■ Information technology security ... up the TAP, since it can be considered the core outcome of the pre -assessment site visit .The TAP is the primary deliverable created during the pre -assessment phase...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 1 docx
... drive the assessment effort. Ultimately, the majority of information is the same in either www.syngress.com Laying the Foundation for Your Assessment • Chapter 1 3 Contracting and the NSA IAM NSA ... of performing assessments the way NSA does. To recap, the IAM trains the individuals in the IAM standard, while the IA- CMM appraises the organization’s ab...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 2 ppt
... prior to the arrival of the assessment team. www.syngress.com 38 Chapter 1 • Laying the Foundation for Your Assessment 286 _NSA_ IAM_ 01.qxd 12/ 15/ 03 3: 15 PM Page 38 Introduction The Pre -Assessment ... with scoping the assessment. www.syngress.com 20 Chapter 1 • Laying the Foundation for Your Assessment 286 _NSA_ IAM_ 01.qxd 12/ 15/ 03 3: 15 PM Page 20 Q: How...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 3 ppt
... Determining the Organization’s Information Criticality 286 _NSA_ IAM_ 03.qxd 12/11/03 3: 25 PM Page 102 no impact on the organization for that particular information type .The number 5, on the other hand, ... have the appropriate pieces in place to create the OICM.This is one of the primary deliverables of the IAM assessment; it defines much of the key information that...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 4 pot
... 12/11/03 3: 25 PM Page 107 In the majority of assessments, the values for each block within the SCMs will be carried directly over from the OICM. Because of the top-down nature of the NSA IAM, the OICM ... the columns across the top of the matrix with the names of the impact attributes we’ll be using for the assessment. The rows are labeled along the lef...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 6 pdf
... Pl. Desk Phone 55 5 .55 5.6826 Mobile Phone/Pager 55 5 .55 5.3162 E-mail lx.roulls@sec.cons.extra Mission Next we move on to the second point of the IAM TAP, the mission statement. We discussed the mission ... 87234 NW Safe Pl. Desk Phone 55 5 .55 5.6832 Mobile Phone/Pager 55 5 .55 5.3762 E-mail bm.high@sec.cons.extra SCE Alternate Point of Contact: Lynn X. Roulls Title Senior...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 7 doc
... questions that will help the assessment team gain the needed information and identify the organization’s vulnerabilities .The first resource for questions comes from the security expertise of the assessment ... feedback from the departments that the assessment was going better than they expected and that they found value in the information that was being collected.Th...
Ngày tải lên: 13/08/2014, 15:21
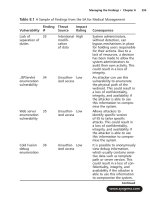
security assessment case studies for implementing the nsa iam phần 8 docx
... have to map the finding to the OICM, or can you just map it to the SICM? A: As you have already learned, the impact definitions are the same for both the OICM and the SICM.Therefore, the findings ... click on the “Ask the Author” form. You will also gain access to thousands of other FAQs at ITFAQnet.com. 286 _NSA_ IAM_ 08.qxd 12/ 15/ 03 5: 03 PM Page 307 286 _NSA_ IAM_ 0...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 9 pot
... conduct the assessment. In our case, we describe the NSA IAM as the methodology used to conduct the assessment and the basis for the assessment process. Since this is the main document, the assessment ... anal- ysis. Security Horizon utilized the National Security Agency (NSA) Information Security Assessment Methodology (IAM) to conduct the organizati...
Ngày tải lên: 13/08/2014, 15:21

security assessment case studies for implementing the nsa iam phần 10 pot
... National Security Agency (NSA) Information Security (INFOSEC) Assessment Methodology (IAM) assessment plan attached to final report, 354 – 355 mission definition and, 68 review in closeout meeting, 3 15 319 See ... 355 –362 creating/formatting, 3 45 355 286 _NSA_ IAM_ Index.qxd 12/17/03 10:31 AM Page 420 418 Index defining, 159 –162 defining in case study, 174–1 75 defining sys...
Ngày tải lên: 13/08/2014, 15:21