Working with Database and Security in Java - Cryptography docx
Working with Database and Security in Java - Cryptography docx
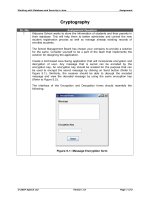
... Working with Database and Security in Java Assignment © 2007 Aptech Ltd Version 1.0 Page 2 of 2 Figure 5.2: Message
Ngày tải lên: 02/08/2014, 08:21

Working with Database and Security in Java - Cryptography (tt) doc
... Working with Database and Security in Java Assignment © 2007 Aptech Ltd Version 1.0 Page 2 of 2 Figure 5.2: Message
Ngày tải lên: 02/08/2014, 08:21

Working with Database and Security in Java - Digital Signatures ppsx
Ngày tải lên: 02/08/2014, 08:21
Working with Database and Security in Java - Java Security doc
Ngày tải lên: 02/08/2014, 08:21

Working with Database and Security in Java - Java Security docx
Ngày tải lên: 02/08/2014, 08:21



CRYPTOGRAPHY AND SECURITY IN COMPUTING pptx
... which were established in 194 8-1 949, have been published in 1966 only, by his student R. Burk. 28 Cryptography and Security in Computing 12 Will-be-set-by -IN- TECH Theorem 10 and Corollary 11 generalize ... Will-be-set-by -IN- TECH results in deciding that P holds on P but does no longer hold when considering a (t + 1)-th testing T t+1 . In terms of security, strong si...
Ngày tải lên: 28/06/2014, 17:20

Chapter 9: Working with Selections and Selection Layers
... options for the Join Line tool, as shown in Figure 1 0-1 0. Figure 1 0-1 0: The Join Line Tool Options palette. Figure 1 0-9 : Before and after using the Join Line tool. 197 Chapter 10: Inking Your Work 16_129869 ... 1 0-7 : Filling a section with All Layers off and on. 196 Part III: Refining and Exporting Your Work 16_129869 ch10.qxp 11/29/07 11:58 AM Page 196 Inking in...
Ngày tải lên: 27/08/2012, 14:31
- working with files and directories in perl
- working with files and directories in ruby
- working with files and directories in unix pdf
- working with files and directories in vb net
- working with files and directories in c
- working with files and directories in linux
- working with files and directories in php
- working with files and directories in unix
- working with files and directories in python