The Illustrated Network- P19 doc

The Illustrated Network- P19 doc
... propagate the ARP packets onto the other LAN segment. Hosts then sent frames to the router, but acted as if they were sending the frames directly to the destination host. Proxy ARP makes sure that the ... process. The message asks for the MAC address associated with the destination, and the sender’s address that should receive the reply. Other devices that hear the...
Ngày tải lên: 04/07/2014, 07:20

The Illustrated Network- P1 docx
... and Interfaces 27 Encapsulation 28 The Layers of TCP/IP 30 The Physical Layer 30 The Data Link Layer 32 The Network Layer 35 The Transport Layer 38 The Application Layer 41 Session Support ... xxiii About the Author xxx PART I Networking Basics CHAPTER 1 Protocols and Layers 3 The Illustrated Network 7 Remote Access to Network Devices 8 File Transfer to a Router 1...
Ngày tải lên: 04/07/2014, 07:20

The Illustrated Network- P2 docx
... Simple Network Management Protocol 609 SNMP Capabilities 612 The SNMP Model 616 The MIB and SMI 618 The SMI 618 The MIB 620 RMON 622 The Private MIB 622 SNMP Operation 623 SNMPv2 Enhancements ... 390 BGP and the IGP 391 Other Types of BGP 392 BGP Attributes 393 BGP and Routing Policy 395 BGP Scaling 395 BGP Message Types 396 BGP Message Formats 397 The Open Mess...
Ngày tải lên: 04/07/2014, 07:20

The Illustrated Network- P5 docx
... and the fi le listing of the default directory on the router, which is /var/home/remote (the router uses the Unix fi le system). The listing in the lower right section is the contents of the ... look at the IETF in detail shortly. The Internet uses more than protocol standards developed by the IETF. The following organizations are the main ones that are the sourc...
Ngày tải lên: 04/07/2014, 07:20
The Illustrated Network- P9 doc
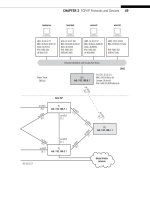
... Inside the frame is the data unit of the IP layer, the packet. The unit of the transport layer is the segment in TCP and datagram in UDP. The segment or datagram by defi nition is the content of the ... (hard- ware) and the memory address space of the application on the host (software). The names of the protocol data units used at each layer are worth reviewing....
Ngày tải lên: 04/07/2014, 07:20

The Illustrated Network- P11 doc
... of Ethereal on the servers). However, LANs are not the only type of connections used on the Illustrated Network. Displaying SONET Links What about link types other than Ethernet? ISPs in the ... connect the nodes of the Illustrated Network. We’ll investigate the frame types used in various technolo- gies and how they carry packets. We’ll take a long look at Ethernet, and m...
Ngày tải lên: 04/07/2014, 07:20

The Illustrated Network- P21 docx
... link at 155 Mbps and the LAN runs at 100 Mbps. There is also no other traffi c on the network, so the transfer rate is totally dependent on the ability of the host to fi ll the pipe from server ... fragments, and the other is the lack of knowledge on the part of a destination of the reassembled datagram size. Let’s look at the destination host reassembly process to e...
Ngày tải lên: 04/07/2014, 07:20

The Illustrated Network- P23 docx
... others do not fall neatly into either category. The structure of the fi elds following the checksum depends on the type of ICMP message. These two formats are shown in Figure 7.5. Note that the ... pairs, and the sequence numbers help sort out queries sent by the same process (the process identifi er, the PID, is often the ICMP Query identifi er in Unix systems). The suit...
Ngày tải lên: 04/07/2014, 07:20

The Illustrated Network- P40 docx
... routers, or ASBRs, run OSPF on the internal links within the AS, but not on the external links to the other AS (this is where we’ll run the EGP). The relationship between the OSPF use of a reference ... a way to cut down on the size of the link-state database, the amount of information fl ooded, and the time it takes to run the SPF algorithm, at least on areas other t...
Ngày tải lên: 04/07/2014, 08:20

The Illustrated Network- P41 docx
... password, but the use of AuType = 2 authentication gives the authentication fi eld the structure shown in the fi gure. In this case, the Key ID identifi es the secret key and authentication algorithm ... create the message digest, the Authentication Data Length specifi es the length of the message digest appended to the packet (which does not count as part of the packet...
Ngày tải lên: 04/07/2014, 08:20